
Lessons from 3 real-life bot attacks
In a recent Threat Spotlight, we looked at Barracuda research on bot attacks and the ways bad bot traffic is changing. Barracuda researchers have been tracking bots on the internet and their effect on applications for several years now, and analyzing those traffic patterns for the first six months of 2023 they identified several interesting trends in the percentage of internet traffic coming from bad bots and where these attacks are originating.
To help you better understand the variety of bot attacks and the impact they can have on all types of organization, Barracuda’s researchers did a deep dive on three different real-life attacks. In each example, they walk through the tactics attackers used, what they were attempting to do, and the ways Barracuda’s security solutions caught the attack and stopped it.
Lesson 1: Ways attacks attempt to hide attacks
In this example, a leading research and software provider for chemistry data faced an issue where they were attracting high volume of bot traffic from a nation-state actor attempting to take over accounts and steal research data. The attacks were slowing down the site significantly, which was having a negative impact on customer experience. More importantly, attackers managed to steal some research, and stopping that from happening again was a serious concern.
To put identify and stop these bots, the customer set up Barracuda Web Application Firewall and Advanced Bot Protection. Once in place, the solutions found many advanced persistent bots, continuous account takeover (ATO) attacks and crawling, and multiple IP addresses from various internet service providers (ISPs) and anonymous system numbers (ASNs), including residential IP addresses.
For example, the traffic pattern below shows a low and slow attack with a relatively low number of requests to try to avoid detection. The bot also used a common user agent to attempt to blend in with the crowd and tried changing IP addresses and locations.
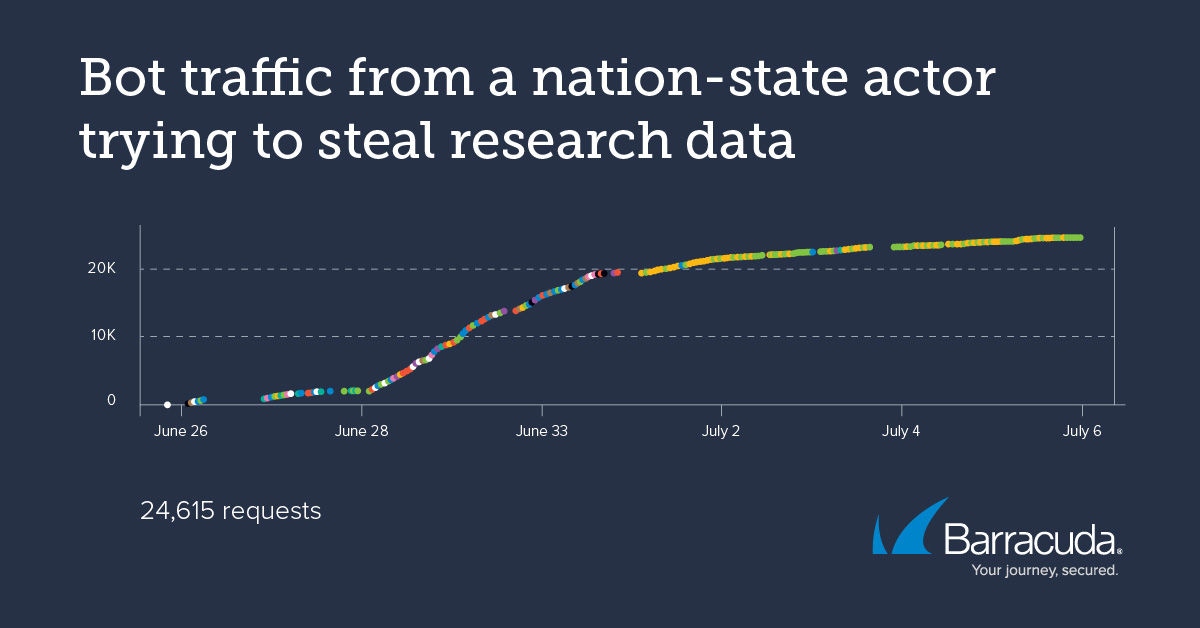
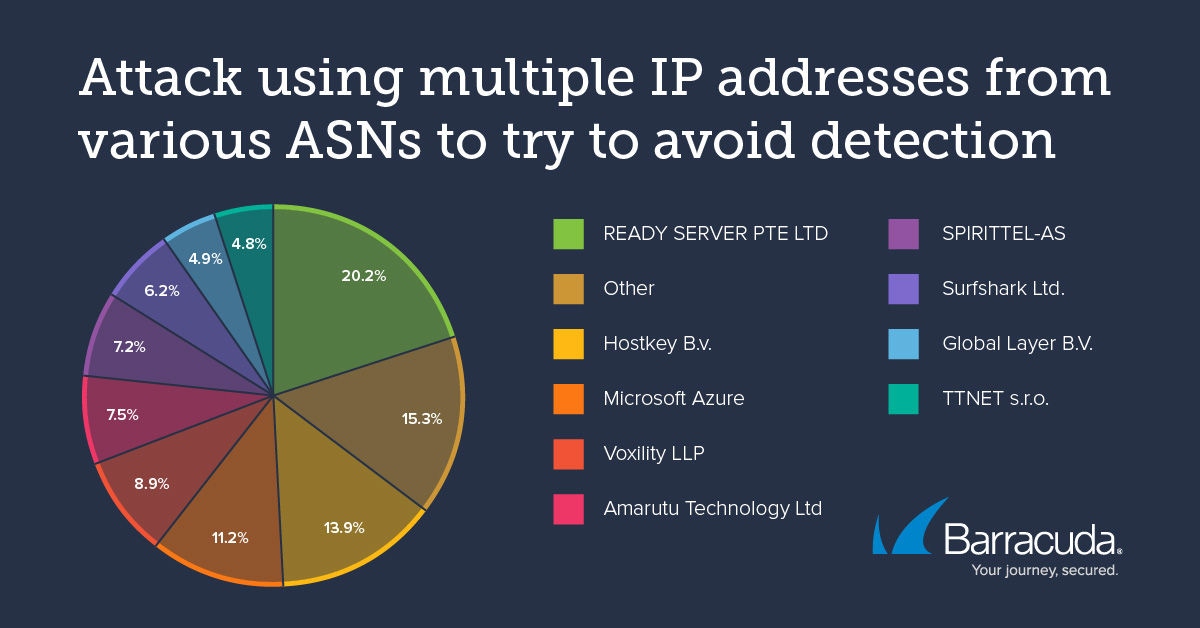
Barracuda Advanced Bot Protection, powered by machine learning, easily detected and mitigated this attack, preventing thousands of account takeover attacks every hour, reducing costs and the load on the security team, and improving the end-user experience.
Lesson 2: A single bot can masquerade as multiple attackers in DDoS attacks
In this example, a SaaS solution handling practice management and point-of-sale software for healthcare practices saw a sudden load on the SaaS solution that made it unavailable to customers. Investigate showed that some of their customers were under heavy ATO attack from distributed bots, with up to 10,000 requests per minute for individual practices via the login API endpoints.
The organization attempted to stop the attacks by using rate limiting and other mechanisms. Then they introduced Barracuda Advanced Bot Protection, which identified a single bot that was attempting to hide in various ISPs and ASNs and while attempting ATO attacks.
Barracuda Advanced Bot Protection blocked more than 4.5 million login attempts in a single day across multiple end customer pages. The bot kept up this volume of attacks for several days before finally giving up. With Barracuda Advance Bot Protection in place, user experience and uptime both improved.
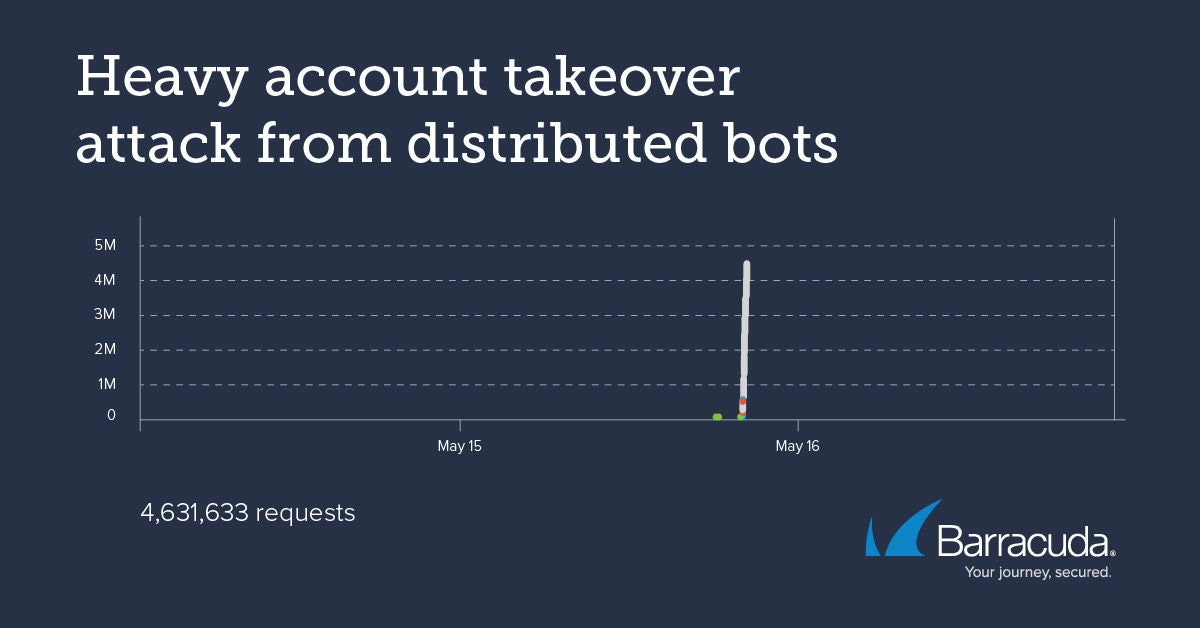
Lesson 3: Bots can adapt to your defenses
In our last example, the login page of an online bookstore was being attacked by bots, leading to reduced availability. The store was also experiencing many false alarms and issues with the backend application. The operations team identified an orchestrated attack from specific regions. When one region was blocked, the attacker simply shifted regions. Rate limits were implemented, but the bot then adapted to the rate limits and moved to low-and-slow distributed attacks.
After the customer implemented Barracuda solutions, Barracuda Advanced Bot Protection identified the bot operating in short bursts while using evasive techniques. These techniques included attempting to learn the rate limits and then avoiding the triggers for the rate limits. The bot was also rapidly cycling through locations and identities to attempt to evade detection.
The images below show examples of different patterns by one bot on various dates, all of which were blocked.
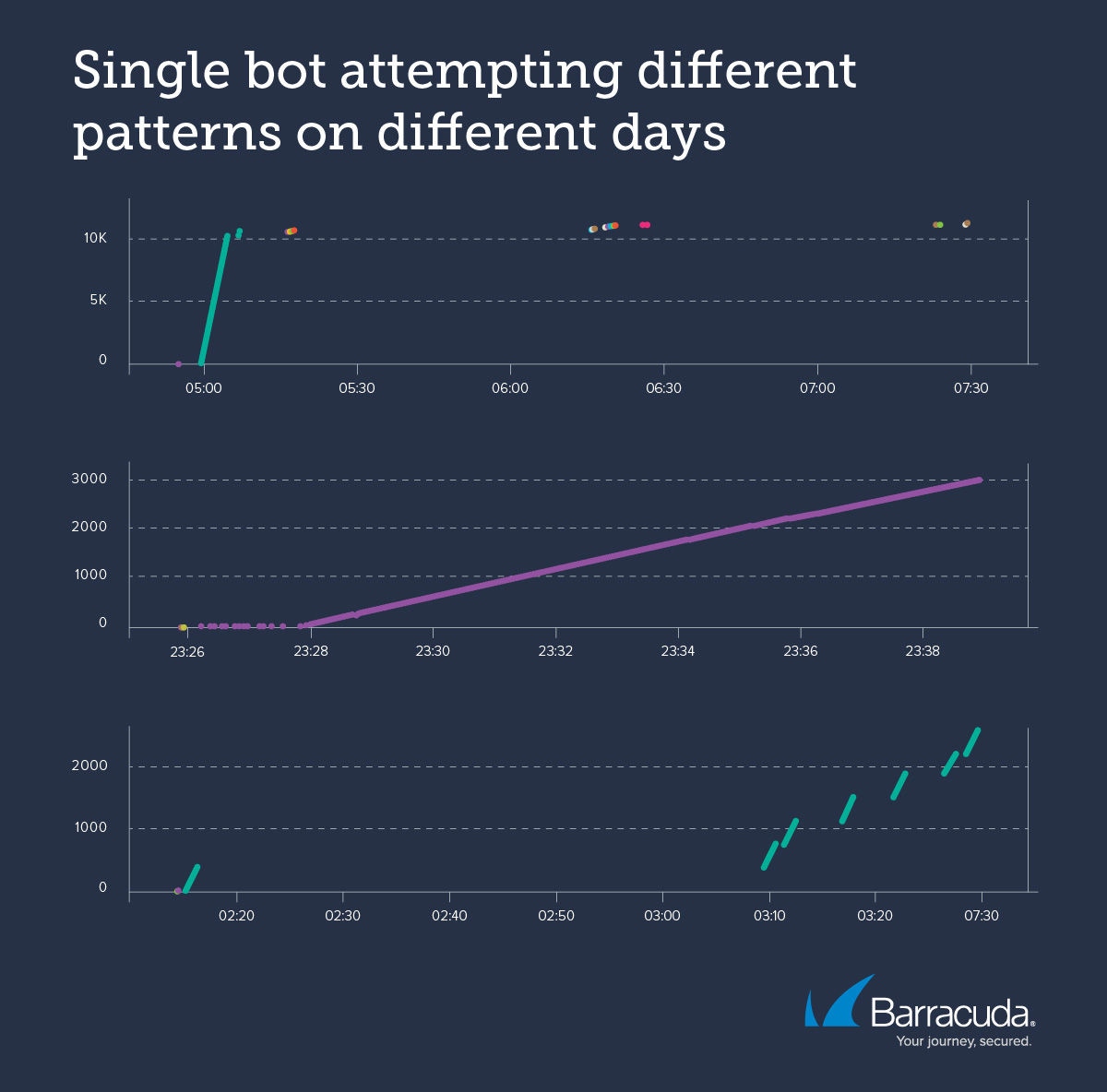
Barracuda Advanced Bot Protection used machine learning to identify the similarities between the bots in order to detect and block the attacks. This stopped the botnet in its tracks, which improved availability and user experience.
Lesson 4: Advanced defenses can make a big difference
An additional lesson that came up in all three examples is how much of an impact having the right solution in place can have. Again and again, we’ve observed the power Advanced Bot Protection has to see past the tricks bots use to try to avoid detection, foil their attacks, and keep businesses up and running.
To protect your business, as well as your data, analytics, and inventory, you need to invest in Web Application and API Protection (WAAP) technology that identifies and stops bad bots. This will improve both user experience and overall security.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





