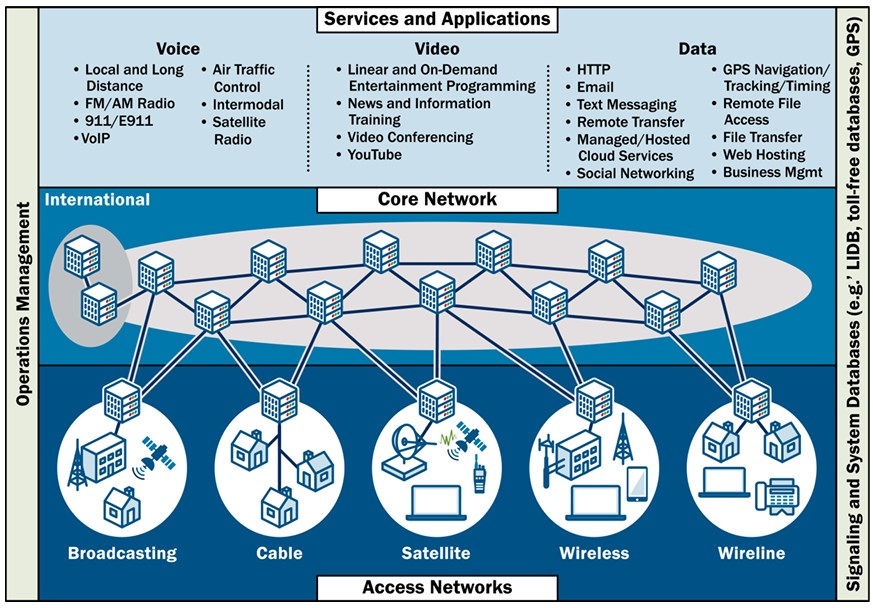
Defensa de Infraestructura: Sistemas de comunicaciones
El sector de las comunicaciones es un facilitador clave en las operaciones de casi todas las demás infraestructuras e industrias. Se considera uno de los cuatro sectores fundamentales e incluye múltiples dominios como la banda ancha móvil, la computación en la nube, la radiodifusión y las redes que soportan internet y otros sistemas de información. Estos sistemas se ilustran parcialmente aquí:
El sector de comunicaciones moderno es casi irreconocible para aquellos que lo definieron por primera vez hace treinta años. La Orden Ejecutiva 13010 (EO 13010) de 1996 identificó las telecomunicaciones como uno de los ocho sectores vitales para la defensa y seguridad económica de los Estados Unidos. La EO13010 reconoció tanto las amenazas físicas como cibernéticas y proporcionó la primera definición formal de infraestructura crítica. El sector de telecomunicaciones se centraba en los sistemas y redes de telecomunicaciones tradicionales.
La Directiva Presidencial 63 (PDD-63) de 1998 amplió el alcance de las ciberamenazas, aumentó los sectores de infraestructura crítica y asignó agencias federales específicas para liderar los esfuerzos gubernamentales con cada sector. También se actualizó la terminología para reflejar un conjunto más amplio de industrias y funciones dentro de cada sector. Esto nos trajo el Sector de Comunicaciones, que fue más inclusivo con las tecnologías emergentes y nuevos sistemas de información.
El sector de las comunicaciones tiene amplias interconexiones con prácticamente todas las demás infraestructuras críticas. Aquí hay algunos detalles sobre sus interdependencias con los otros tres sectores fundamentales:
Sector |
Dependencias de las comunicaciones |
Dependencias de Comunicaciones en el Sector |
Transporte |
- Sistemas de gestión del tráfico y navegación en tiempo real |
- Apoyo a la infraestructura (por ejemplo, líneas de fibra óptica a lo largo de rutas de transporte) |
Energía |
- Monitoreo y control de las operaciones de la red eléctrica (sistemas SCADA) |
- Suministro eléctrico fiable para sistemas de comunicación |
Agua |
- Sistemas de Control y Adquisición de Datos (SCADA) para el tratamiento y distribución de agua |
- Agua para enfriar equipos de comunicación (por ejemplo, centros de datos) - Dependencia de las compañías de agua para actividades de mantenimiento |
Estas interdependencias crean un paisaje de riesgo complejo, donde una interrupción en un sector puede tener efectos en cascada en múltiples otros.
¿Quién está a cargo?
La propiedad de los activos en el sector de las comunicaciones implica una combinación de empresas privadas, entidades públicas y estructuras híbridas, con cientos de empresas operando dentro de varias industrias. Ejemplos:
Propietarios del sector privado
Corporación Pública: Verizon Communications Inc. posee y gestiona una extensa red de torres celulares, cables de fibra óptica y otros activos de comunicaciones críticos.
Empresas Privadas: Diamond Communications posee y gestiona más de 4,000 sitios de comunicación inalámbrica alquilados, propiedades de antena distribuida y otros activos.
Propietarios del sector público
El Departamento de Defensa de los EE. UU. (DoD) posee y opera múltiples sistemas de comunicaciones, incluyendo la Red de Sistemas de Información de Defensa (DISN), el Sistema de Comunicación de Inteligencia Mundial Conjunta (JWICS), y los Sistemas de Transmisión del Ejército y Comunicaciones de Defensa (DCATS). El DoD es uno de los mayores propietarios del sector público de infraestructura crítica en los EE. UU.
Estructuras de Asociación Híbridas
La Main Connectivity Authority es una asociación público-privada en el sector de las comunicaciones. Esta organización estatal existe para expandir los servicios de banda ancha a áreas rurales y otras comunidades en Maine. Con este fin, el gobierno estatal se asocia con múltiples empresas privadas que pueden ofrecer estos servicios.
Asociaciones Público-Privadas (PPPs)
La Autoridad de Banda Ancha de la Costa Este de Virginia es una asociación entre los condados de Accomack y Northampton. Esta autoridad construyó una infraestructura de banda ancha de medio recorrido a lo largo de los dos condados rurales y la puso a disposición de las comunidades locales y los proveedores de servicios privados.
El sector privado posee la mayoría de los activos de comunicación en los Estados Unidos. Dado que los propietarios y operadores son responsables de la seguridad de sus activos, el sector privado es responsable de asegurar la mayor parte de la infraestructura de comunicaciones en los EE. UU.
Cada sector tiene una Agencia de Gestión de Riesgos del Sector (SRMA) y Plan Específico del Sector (SSP) destinado a ayudar a los propietarios y operadores a gestionar los riesgos actuales. Aunque el desarrollo del SSP es obligatorio, la implementación de las orientaciones del SSP es casi siempre voluntaria para el sector privado y otras entidades no federales.
El Departamento de Seguridad Nacional de los EE. UU. (DHS) es la Agencia de Gestión de Riesgos del Sector (SRMA) para el Sector de las Comunicaciones. La Agencia de Seguridad de Infraestructura y Ciberseguridad (CISA) es la agencia que desempeña estas funciones de SRMA. El SSP de Comunicaciones está publicado aquí.
Riesgos y desafíos
Un informe de 2021 de la Oficina de Responsabilidad del Gobierno de los Estados Unidos (GAO) resumió los riesgos para el sector de las comunicaciones en un informe de 43 páginas que identificó tres cuestiones clave:
- CISA no había evaluado el rendimiento de su apoyo al sector de las comunicaciones. No había métricas ni mecanismos de retroalimentación para medir la eficacia.
- CISA no había completado una evaluación de capacidades para su función como coordinador federal de respuesta y recuperación de incidentes. Puede haber brechas desconocidas en recursos o personal.
- CISA no ha actualizado el Plan Sectorial de Comunicaciones de 2015 para reflejar amenazas y riesgos nuevos y emergentes, así como sus responsabilidades legales. La SRMA recomienda que todos los SSPs se actualicen cada cuatro años.
La GAO incluyó recomendaciones para la acción ejecutiva para abordar estos temas clave. A fecha de redacción, estas recomendaciones siguen abiertas / sin realizar.
Es importante recordar que el SSP solo proporciona orientación, y ninguna entidad está obligada a seguir las recomendaciones. Sin embargo, el SSP aborda las condiciones operativas únicas y el panorama de riesgos que enfrenta el sector. Debido a que el SSP está actualmente desactualizado, carece de orientación sobre amenazas nuevas y emergentes para la cadena de suministro de tecnología de comunicaciones, o interrupciones en los servicios de posición, navegación y sincronización.
Otros desafíos son similares a los que se encuentran en muchas otras industrias: sistemas heredados que son críticos para la misión pero están obsoletos y sin soporte, vulnerabilidades en la cadena de suministro bajo control de terceros, y fragmentación de infraestructura que crea prácticas de seguridad inconsistentes entre proveedores.
Ataques cibernéticos en curso y daños
Al menos nueve proveedores de comunicaciones de EE. UU. han sido comprometidos por Salt Typhoon, un actor de amenaza afiliado a la República Popular China (RPC). Este grupo ha estado apuntando a comunicaciones y otras infraestructuras críticas en todo el mundo desde al menos 2020. Los investigadores creen que este grupo estaba apuntando a hoteles, gobiernos y bufetes de abogados desde 2019, pero no fue identificado hasta más tarde. El Buró Federal de Investigaciones (FBI) de EE. UU. y CISA confirmaron la afiliación de Salt Typhoon con la RPC.
Salt Typhoon es conocido por varios otros nombres, como FamousSparrow, GhostEmperor y UNC2286. El grupo utiliza una variedad de tácticas, técnicas y procedimientos (TTPs) sofisticados en sus ciberataques:
- Explotación de Vulnerabilidades: El grupo explota tanto vulnerabilidades conocidas como de día cero en sistemas ampliamente utilizados, como Microsoft Exchange (vulnerabilidades ProxyLogon) y Ivanti Connect Secure (CVE-2023-46805, CVE-2024-21887).
- Malware Avanzado: Malware personalizado como "GhostSpider" permite el acceso persistente a sistemas comprometidos.
- Técnicas de movimiento lateral y ocultación: El grupo utiliza una variedad de herramientas para moverse a través de los sistemas y evadir la detección.
Salt Typhoon también utiliza credenciales robadas e infecciones de malware para obtener acceso. Estos son métodos comprobados de compromiso, y deberías asumir que incluso los grupos más sofisticados utilizarán estos métodos.
Se ha vinculado a otros dos afiliados de la RPC con ataques al sector de las comunicaciones. Volt Typhoon y APT41 han infiltrado sistemas aparentemente seguros, a menudo a través de vulnerabilidades sin parchear o previamente desconocidas.
El PRC no está solo en estos intentos de desestabilizar a otros países. Actores de amenazas rusos como Sandworm (GRU Unidad 74455) y APT29 (Cozy Bear, Midnight Blizzard) tienen empresas de infraestructura en muchas naciones occidentales. Sandworm parece centrar sus esfuerzos en Ucrania, mientras que APT29 lleva a cabo ataques globales.
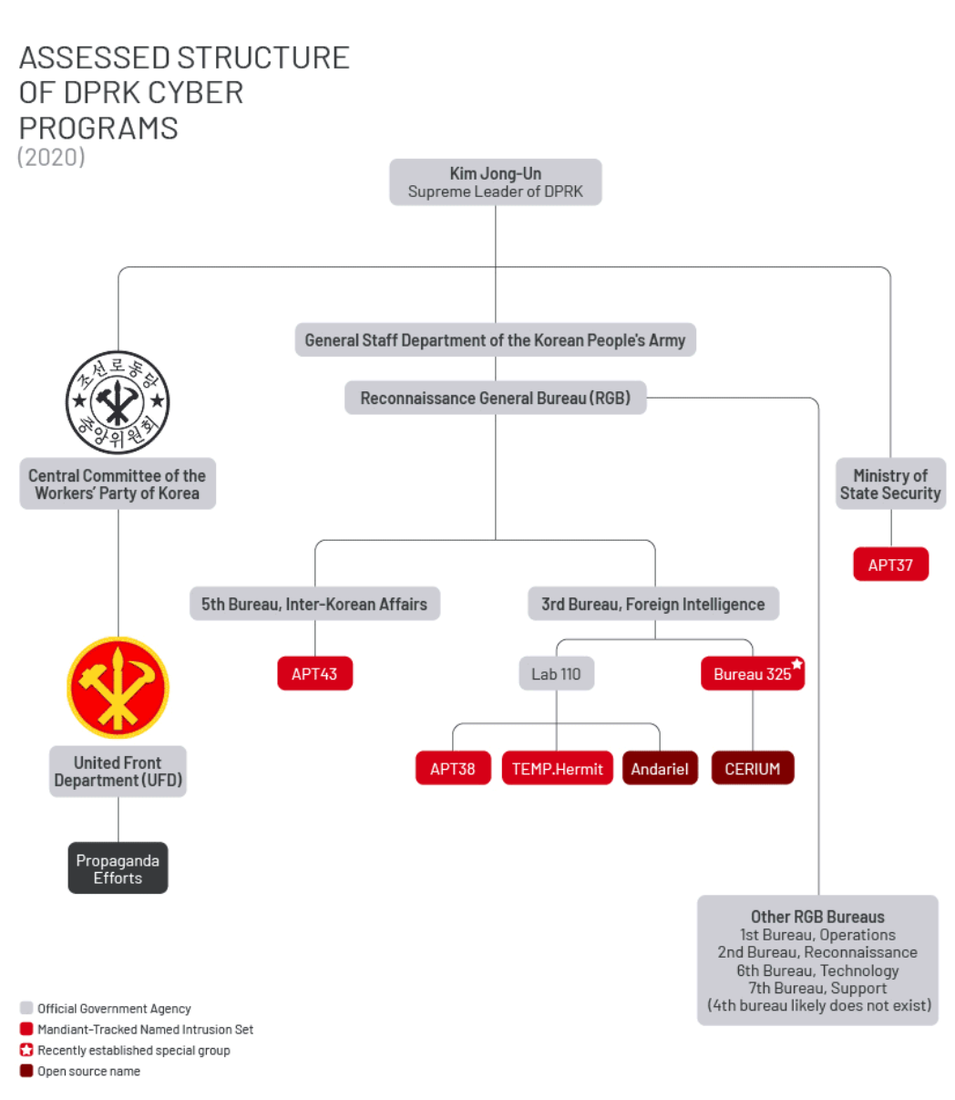
Varios grupos afiliados a la República Popular Democrática de Corea (RPDC, Corea del Norte) han sido implicados en ataques a las comunicaciones de EE.UU. Grupos de amenazas como Andariel (APT45), Kimsuky (APT43) y Grupo Lazarus han infiltrado infraestructuras críticas de EE.UU. para apoyar al régimen norcoreano. Los investigadores de Mandiant han publicado esta ilustración de las relaciones entre los actores de amenazas de la RPDC y el régimen de Kim Jong-Un:
Todos estos grupos están motivados por el espionaje, el posicionamiento estratégico y el beneficio económico. Es difícil calcular el daño causado por estos ataques, pero sabemos que hay pérdidas económicas significativas y exposición de datos confidenciales. También ha habido interrupciones operativas, que amplifican los costos más allá del ámbito de la recuperación de incidentes.
Guía para los operadores de sistemas de comunicación
Los operadores de infraestructura de comunicaciones deben seguir estas mejores prácticas y procedimientos:
- Segmentación de red para limitar el movimiento lateral y aislar sistemas críticos y datos sensibles.
- Métodos de autenticación robustos diseñados para resistir el phishing y otros ataques basados en credenciales.
- Desactiva todos los servicios y protocolos innecesarios en los dispositivos de red, mantén actualizadas las versiones del sistema operativo y aplica los parches de seguridad con prontitud.
- Educar al personal sobre las mejores prácticas de ciberseguridad, incluyendo cómo identificar intentos de phishing y la importancia de seguir los procedimientos de seguridad de la empresa.
- Desarrollar un plan de respuesta a incidentes y realizar evaluaciones de seguridad periódicas.
- Evaluar y supervisar las prácticas de seguridad de los proveedores y suministradores para mitigar los riesgos asociados con el acceso de terceros a sistemas y datos.
Orientación al público
Una de las responsabilidades más importantes del público es proteger las credenciales y la identidad. Utilice contraseñas seguras y MFA, tenga cuidado con los intentos de phishing y los enlaces o descargas sospechosas y sea consciente de compartir información personal en las redes sociales. Utilizar conexiones Wi-Fi seguras y proteger el acceso a los dispositivos personales son también medidas fundamentales.
No se puede negar que la infraestructura crítica es un asunto de seguridad nacional. Cada operador en estos sistemas debe fomentar una cultura de conciencia de seguridad y practicar una buena higiene cibernética. También es importante que las partes interesadas aprovechen sus asociaciones y otros sistemas de apoyo. No podemos asegurar adecuadamente la infraestructura de comunicaciones sin un enfoque colaborativo que involucre al gobierno, la industria y el público.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.