
Threat Spotlight: The evolving use of QR codes in phishing attacks
KEY FINDINGS
- Barracuda threat intelligence researchers have detected more than half a million phishing emails with quick response (QR) codes embedded in PDF documents.
- QR codes that lead to phishing websites are now being included in PDF documents and attached to emails — versus being included in the emails themselves.
- The attacks are designed to capture login credentials for compromise.
UNDERSTANDING THE THREAT
QR code phishing, also known as quishing, is a type of social engineering attack. Cybercriminals try to trick victims into using the camera on their mobile phone to scan a QR code that goes to a malicious website to steal sensitive information, such as login credentials or financial data.
Cybercriminals are evolving the ways in which they are using QR codes to carry out attacks. In the three-month period from mid-June to mid-September, Barracuda researchers identified and analyzed more than half a million phishing emails with QR codes embedded in PDF documents. The PDFs are attached to phishing emails that use brand impersonation and urgency to motivate would-be victims to respond. This is a notable change in tactics: In the past, QR codes were traditionally included in the body of the phishing emails.
Quishing attacks by the numbers
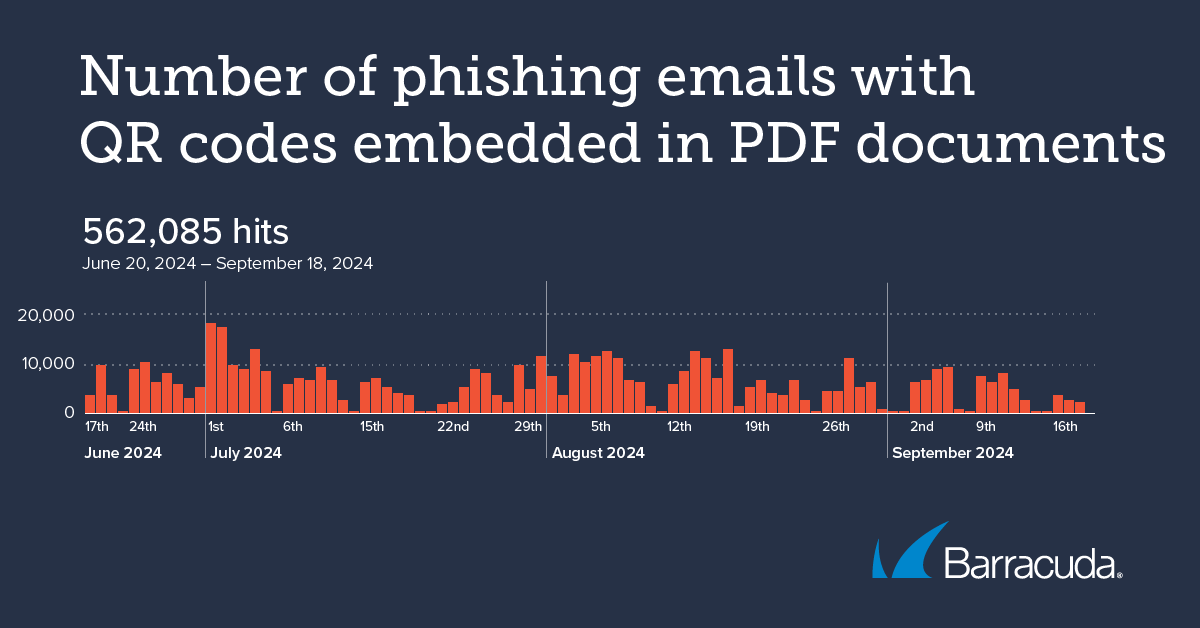
In a three-month period, Barracuda researchers identified and analyzed more than half a million phishing emails with QR codes embedded in PDF documents.
In most of the attack samples analyzed by Barracuda researchers, scammers impersonate well-known companies. Microsoft, including SharePoint and OneDrive, is impersonated in more than half (51%) of all the attacks, followed by DocuSign (31%), and Adobe (15%). In a small number of the attacks, scammers impersonate the human resources department at the intended victim’s company.
In these attacks, cybercriminals send phishing emails and attach a simple one or two-page PDF document that includes a QR code. No other external links or embedded files are included in the PDF. Recipients are directed to scan the QR code with the camera on their mobile phone, so they can view a file, sign a document, or listen to a voice message. If they do so, they are brought to a phishing website designed to capture their login credentials.
Brands being impersonated
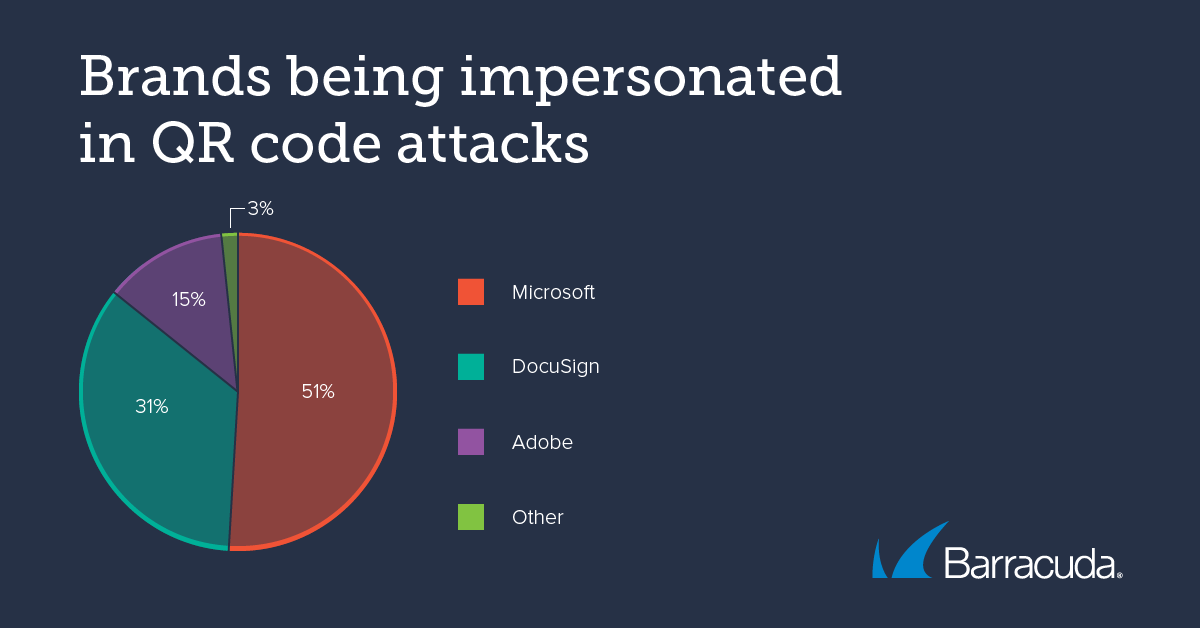
Scammers impersonate well-known brands and use social engineering tactics to trick victims.
Quishing poses some unique security challenges for businesses. Traditional email filters struggle to detect these attacks because there are no direct links or suspicious attachments to scan. Additionally, quishing often involves multiple devices: employees receive the phishing email on one device but scan the QR code using a different device, such as a personal mobile phone that may lack the same level of security protection as corporate systems. As a result, these attacks can bypass corporate defenses, making them difficult to track or prevent.
Certain industries — such as finance, healthcare, and education — are increasingly being targeted by quishing attacks due to the sensitive data they handle. Small-to-medium businesses (SMBs) are especially vulnerable since they often lack the advanced security tools needed to protect against these sophisticated phishing tactics. The shift in tactics from embedding QR codes in the body of an email to attaching them in PDF documents makes it harder for traditional defenses to identify and block these attacks before they reach employees.
EXAMPLES OF QUISHING EMAILS
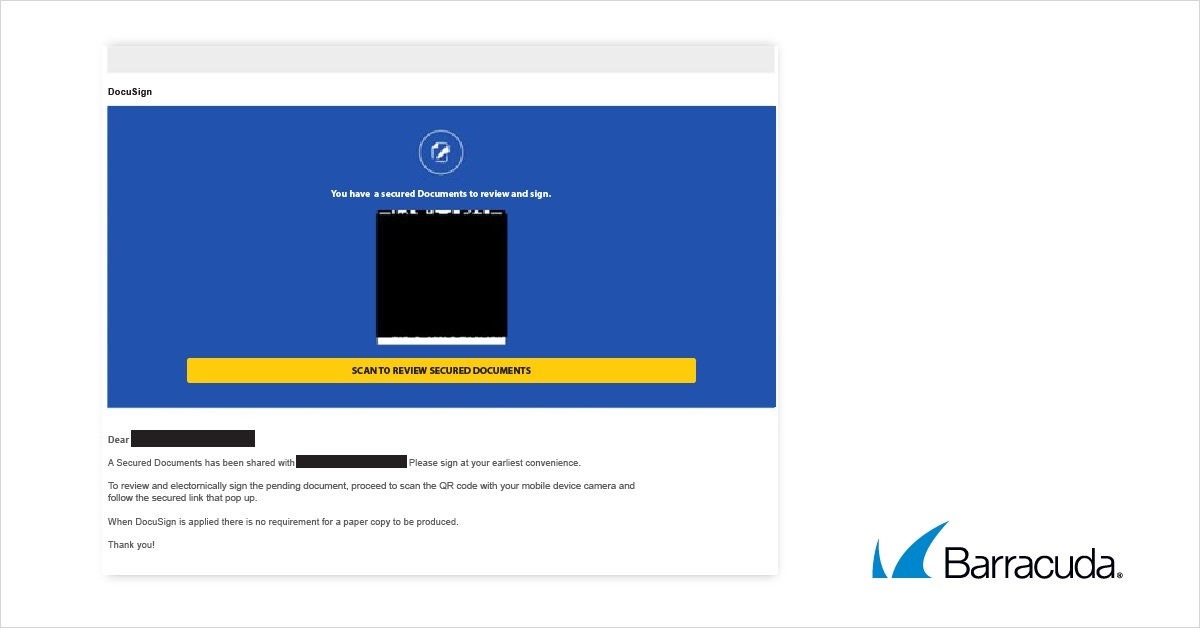
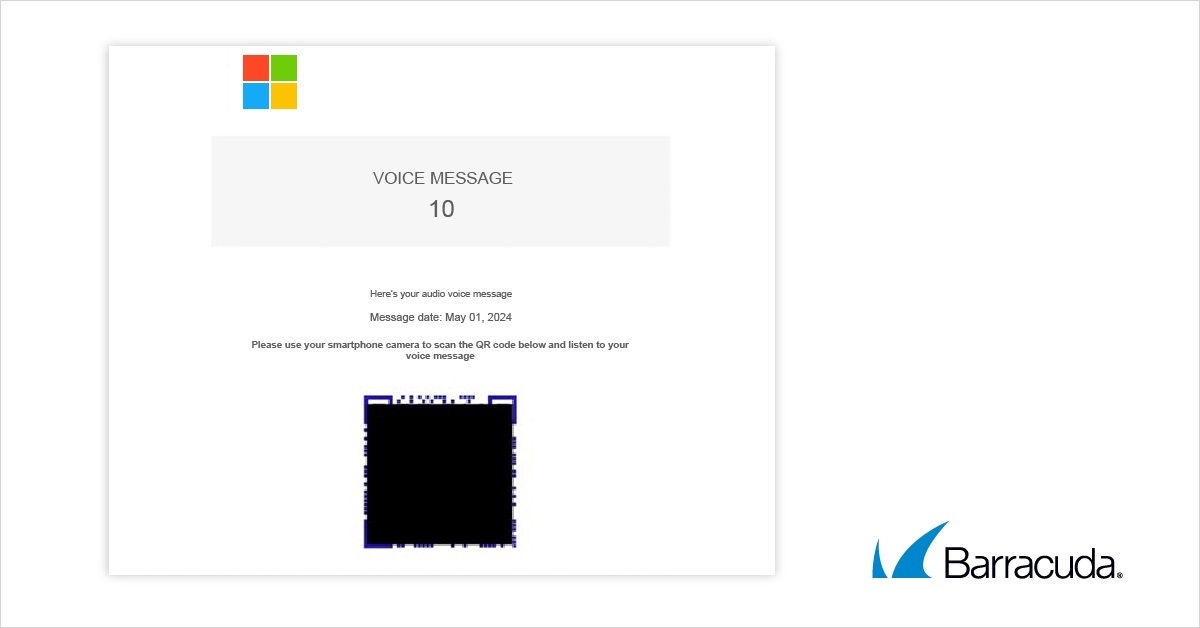
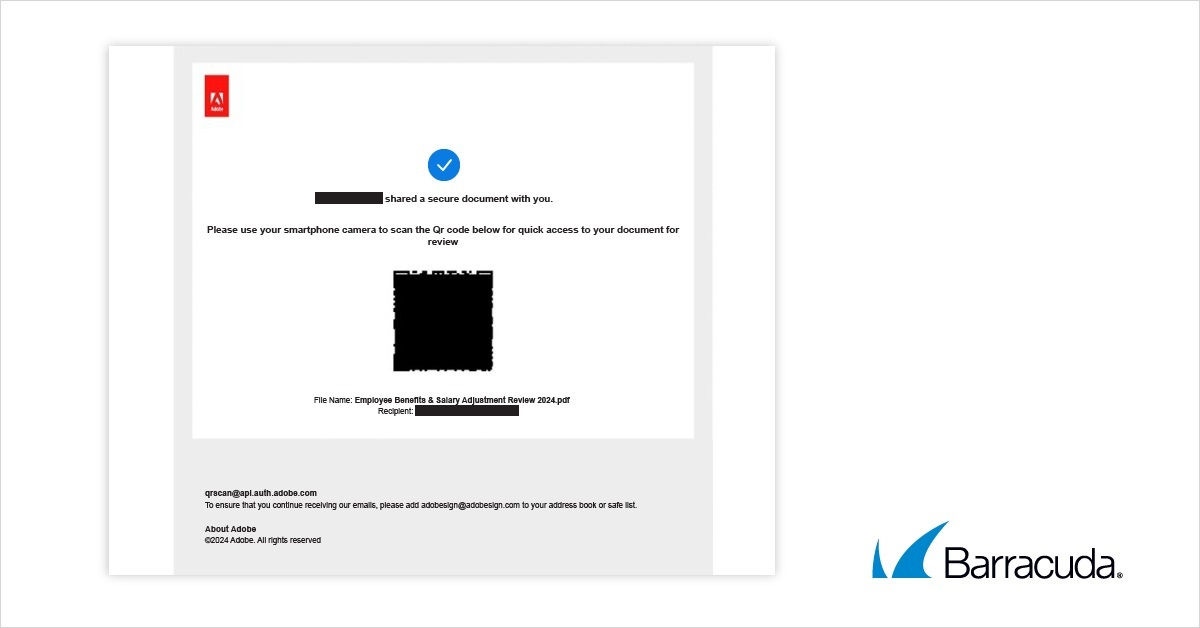
This phishing email that impersonates Adobe tells recipients to scan the QR code in an attached PDF document to review an “Employee Benefits & Salary Adjustment Review” document.
DEFENDING YOUR BUSINESS FROM ATTACKS
Here are several ways to defend against quishing:
Deploy multilayered email security
Put robust spam and malware filters in place and ensure they are properly configured to block phishing messages effectively. IT teams further need to perform a health check on email gateway settings regularly to ensure optimal performance.
Use AI and other advanced technology
Scammers are adapting their tactics to bypass gateways and spam filters, so it’s critical to have a solution in place that detects and protects against targeted phishing attacks. Supplement your gateways with AI-powered cloud email security technology that doesn’t solely rely on looking for malicious links and attachments.
Educate users
Be sure your security awareness training teaches employees about quishing and the risks of scanning QR codes from unknown or questionable sources. Ensure employees can recognize these attacks, understand their fraudulent nature, and know how to report them.
Enable multifactor authentication (MFA)
Provide an additional layer of security above and beyond username and password and reduce the potential impacts of credential compromise by using MFA to protect access to user accounts.
RELATED RESOURCES
[Report] Top Email Threats & Trends ~ June 2024
https://www.barracuda.com/reports/email-threats-and-trends-1
[Blog post] Quishing: What you need to know about QR code email attacks
https://blog.barracuda.com/2023/10/05/quishing-what-you-need-to-know-about-QR-code-email-attacks
[Blog post] Novel phishing techniques to evade detection: ASCII-based QR codes and ‘Blob’ URIs
https://blog.barracuda.com/2024/10/09/novel-phishing-techniques-ascii-based-qr-codes-blob-uri

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





