5 ways AI is being used to improve security: Automated and augmented incident response
Over the last few months, we've been exploring artificial intelligence (AI) and its role in cybersecurity and digital acceleration. If you've missed these posts, you can find them here.
Today, we're exploring how AI can improve the cybersecurity incident response process. Before we begin, let's review the basics of incident response (IR).
What is Incident Response?
While it is technically correct to say that IR is a response to an incident, that level of IR is not sufficient for cybersecurity, and it's not what we're talking about today. We are talking about a higher level of IR that is truly its own domain in cybersecurity. In this context, it is more appropriate to think of IR as a comprehensive set of practices and strategies that actively contribute to the company's security posture. The global incident response market was measured at $23.45 billion in 2021 and is expected to achieve a compound annual growth rate (CAGR) of 23.55% through 2030.
Incident response is a concept, framework, a set of solutions, and much more. IR has grown along with the Internet and other digital technologies and emerged as a structured discipline in the 1980s when Carnegie Mellon University established the first Computer Emergency Response Teams (CERT). More cyberthreats led to more CERTs at all levels. Companies, municipalities, and countries established their own response teams, and by the 2000s, IR was recognized as a critical function. Industry recommendations and guidelines around IR were published in the early 2010s:
- National Institute of Standards and Technology (NIST) Computer Security Incident Handling Guide (Special Publication 800-61)
- SANS Institute Incident Handler's Handbook
The two publications differ in some ways, but both provide a comprehensive structure for an IR strategy:
Aspect |
SANS Incident Handler's Handbook |
NIST SP 800-61 |
Overview |
Practical guide for incident response professionals. |
Comprehensive guide for incident response across organizations. |
Framework Phases |
Six phases: Preparation, Identification, Containment, Eradication, Recovery, Lessons Learned |
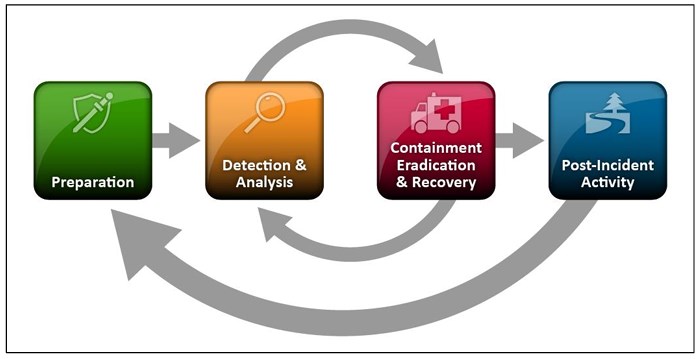
Four main phases: Preparation, Detection and Analysis, Containment, Eradication, and Recovery, Post-Incident Activity. See the image below for how these four phases work together. |
Preparation |
Establishing and training the incident response team, developing IR plans, securing tools and resources |
Developing policies and procedures, establishing an IR team, equipping with necessary tools, conducting training and exercises |
Detection and Analysis |
Identification: Detecting and confirming incidents, categorizing and prioritizing incidents |
Continuous monitoring, incident detection, and confirmation, analyzing the scope and impact of incidents |
Containment |
Implementing short-term and long-term containment strategies to limit the impact |
Short-term and long-term containment measures to isolate affected systems and prevent further damage |
Eradication |
Eliminating the root cause of incidents, removing malware, and closing vulnerabilities |
Identifying and eliminating the root cause, ensuring all malicious artifacts are removed |
Recovery |
Restoring affected systems to normal operations, verifying integrity and security |
Restoring systems and services, verifying their functionality and security post-incident |
Post-Incident Activity |
Lessons Learned: Conducting a post-incident review to improve future response efforts |
Post-Incident Activity: Conducting reviews, documenting lessons learned, updating plans and procedures |
Tools and Techniques |
Practical recommendations on tools and techniques for each phase, including checklists and templates |
Comprehensive discussion on various tools and technologies supporting incident response, including forensic tools and Security information and event management (SIEM) systems |
Communication and Coordination |
Emphasizes the importance of clear communication within the incident response team and with external stakeholders |
Strategies for effective internal and external communication, coordinating efforts during an incident |
Continuous Improvement |
Focuses on regular training, exercises, and updates based on lessons learned |
Emphasizes the need for continuous improvement through regular reviews, updates to policies, and ongoing training |
Use Cases and Examples |
Includes real-world examples and case studies to illustrate key points |
Provides hypothetical scenarios and examples to explain incident response processes |
The NIST guidelines are more detailed and emphasize the development of policies, comprehensive preparation, and continuous improvement. The document is meant to provide a detailed framework that any organization can make into a suitable IR program. The SANS document is more practical and will help you implement your IR program as soon as possible. We'll be using the NIST guidelines in this post.
Incident response began as a reactive and splintered domain and became more structured and formalized as threats proliferated. Perhaps the largest step forward was the collective response to the Year 2000 (Y2K) bug. This was a significant global event that brought attention to incident response and risk management. Y2K led to the development of best practices, cross-industry collaboration, and the establishment of formal IR teams. This event also revealed the importance of proactive measures and early detection, prevention, and mitigation of potential threats. This proactive approach is the foundation for modern IR.
Timeline of incident response and AI enhancements
The most basic explanation of AI is that it refers to computer systems capable of performing tasks that normally require human intelligence. Decision-making is a key outcome, but strong AI also requires other cognitive-like capabilities. Visual perception, speech recognition, and language translation are examples of what may be required by certain AI-enhanced applications.
Several key factors influence the speed of innovation around artificial intelligence. Computational power, data availability, development platforms, and closed- or open-source collaboration are examples of this. Advancements in these areas enable the advancements in AI. Here's a basic timeline of innovation enablers and AI enhancements to incident response:
Decade |
Key Enablers |
AI Integrations in Incident Response Tools |
1990s |
- Increased computational power (Moore's Law (animated explainer video)) - Development of the Internet - Availability of larger datasets - Introduction of graphics processing units (GPUs) for parallel processing |
- Basic rule-based expert systems for threat detection - Early anomaly detection systems - Automated log analysis tools |
2000s |
- Growth of big data - Improved algorithms - Cloud computing infrastructure - Development of open-source libraries |
- Security information and event management (SIEM) platforms incorporate machine learning. - Intrusion Detection Systems (IDS) with machine learning components - Early AI-powered threat intelligence platforms
|
2010s |
- Availability of massive datasets - Advances in processing hardware - Development of deep learning frameworks - Increased investment in AI research and development |
- Security orchestration, automation and response (SOAR) platforms emerge - Advanced AI-powered threat detection and analysis tools - User and entity behavior analytics (UEBA) leverages AI for behavior modeling. - Machine learning is integrated into Endpoint Detection and Response (EDR) solutions |
2020s |
- Quantum computing advancements - Enhanced AI chips and specialized hardware - Increased collaboration between academia and industry - Focus on ethical AI and regulatory frameworks |
- AI-powered autonomous response capabilities - Integration of large language models (LLMs) in IR tools - AI-driven predictive threat intelligence - Quantum-resistant cryptography with AI components - Explainable AI for incident analysis and reporting |
AI and incident response
Barracuda's recently published e-book identifies three IR functions that are significantly enhanced by AI:
Automate incident identification: Al can identify, categorize, and prioritize security incidents based on their severity and potential impact on the organization. Incident identification aims to detect these threats as early as possible to mitigate their impact and protect organizational assets. Automated incident triage accelerates the early stages of incident response and lets security teams focus on the most critical incidents first. This function relies on machine learning algorithms, anomaly detection, and predictive analytics.
Orchestration and playbook automation: An incident response playbook, or runbook, is a detailed, pre-defined set of procedures and instructions that guide an organization's response to specific cybersecurity incidents. The terms playbook and runbook are often used interchangeably, though runbooks are more detailed and often include the exact actions for specific procedures. The orchestration piece is the automated coordination and management of the security tools and systems to streamline and optimize incident response processes. In this domain of incident response, AI will automate routine tasks like blocking malicious IP addresses and isolating compromised systems. Manual labor and response times are reduced.
Increase the effectiveness of security operation center (SOC) teams: SOCs can significantly enhance cybersecurity capabilities by integrating AI. A SOC is a centralized facility with a security team that continuously monitors a company's security posture. The SOC team’s primary goal is to detect, analyze, and respond to cybersecurity incidents using a combination of technology solutions and robust processes. The playbooks are critical tools for SOCs. AI integration improves threat detection by analyzing patterns and anomalies that indicate Al-assisted attacks, ensuring that defenses evolve alongside emerging threats. This enables SOCs to create flexible defense mechanisms that constantly adapt their security strategies in time to combat these advanced threats.
Like this post?
This is part four of five in a series based on a new e-book titled Securing tomorrow: A CISO’s guide to the role of AI in cybersecurity. This e-book explores security risks and exposes the vulnerabilities that cybercriminals exploit with AI to scale up their attacks and improve their success rates. Get your free copy of the e-book right now, and check out these related posts:
- The evolution of artificial intelligence
- Series: 5 ways cybercriminals are using AI
- Series - 5 ways AI is being used to improve security
- Series - A CISO's guide to the role of AI in cybersecurity
- Rewarding talent and exploring generative AI at Cudathon
- How artificial intelligence is changing the threat landscape
Did you know…
Barracuda's multi-tiered global SOC is structured to provide 24x7x365 coverage regardless of your location. Our team of security analysts works with well-documented runbooks and processes, as well as key toolsets, such as Security Information and Event Management (SIEM), Threat Intelligence Platform (TIP) and Security Orchestration, Automation, and Response (SOAR), to ensure quicker time to detection and remediation. Visit our website for more information.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.