Dell: 49 million customer records exposed in 1 automated attack
"We’ve been trying to reach you concerning your laptop’s extended warranty."
A couple of weeks ago, Daily Dark Web reported that Dell had been breached. Rather, they reported that a threat actor was claiming to sell a Dell database containing 49 million customer records. These records covered the information on systems purchased from Dell between 2017 and 2024, and the data had many customer details—including service tags, item numbers, warranty details, addresses, phone numbers, and more. Dell confirmed this breach and alerted victims around May 10, 2024.
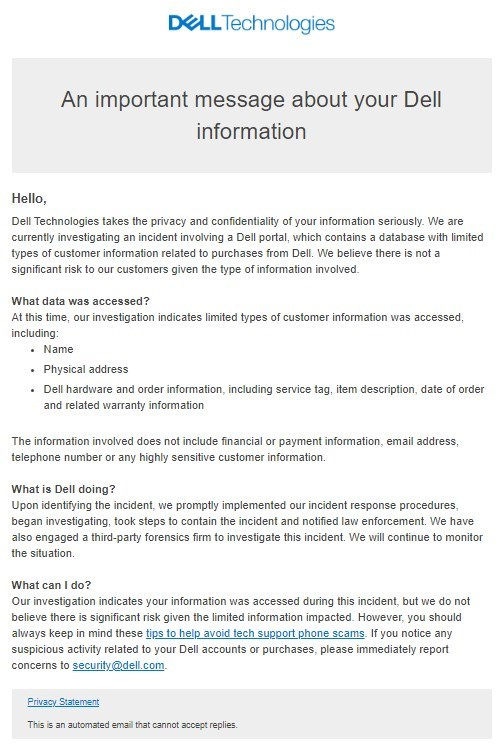
Dell email notification of data breach
The first thought from this was that we were going to see a massive wave of phishing, smishing, and vishing using this data as the bait. This is no doubt in the works (oh joy!), though this author was more concerned about how that actual data was exfiltrated.
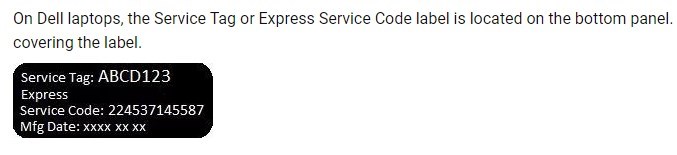
The details of the breach don’t make for comforting reading. The person who scraped the data shared multiple screenshots of emails he had sent Dell regarding the vulnerability which were not responded to – this was confirmed by Dell. The scraping itself was done by brute-forcing an online partner portal. The threat actor registered multiple accounts on the portal as a partner, and these accounts were all approved within 48 hours. Once these accounts were approved, he generated random service tags – these are seven-digit numbers and consonants, so there is a pattern to use for the generation. You can see an example in this image taken from the Dell support website:
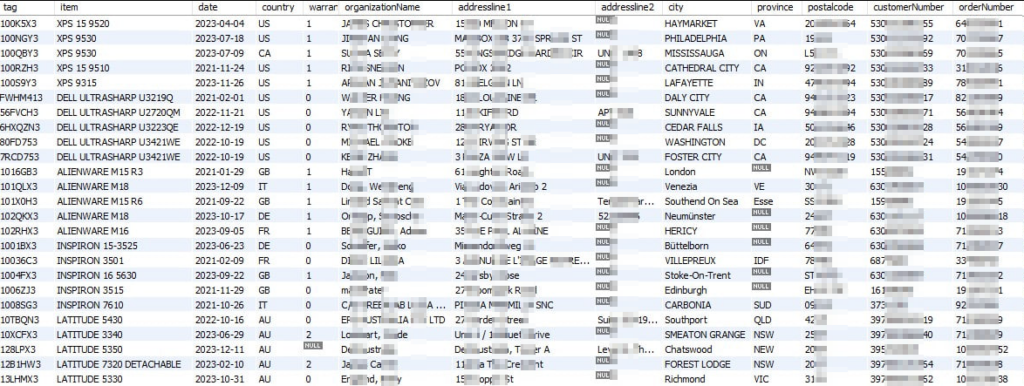
This is a screenshot of a sample of the breached data. You can see the service tag in the left-most column of the data shown here:
The Dell service tag is like a serial number, and it’s used to help customers track product information like technical specifications, documentation, and warranty. Dell’s support system identifies drivers, accessories, and compatible internal components for your product by using this service tag identifier.
The partner portal allowed any level of partner to access this information without any authorization checks on whether the partner was allowed to access the specific customer’s information. The attacker sent about 5000 requests per minute to this page for the duration of the attack. That’s roughly three weeks of a brute force attack that sent over 50 million requests and captured about 49 million customer records. The attacker then sent multiple emails to Dell to disclose the vulnerability. A Dell spokesperson confirmed they received the messages.
This is where it gets murky. TechCrunch reports that Dell had sent the breach notification to some customers whose details are not part of the breach database. However, Dell claims that they were already aware of the incident and “implementing our response procedures and taking containment steps.” Something doesn’t add up, though one thing is certain – as we see frequently, security is an afterthought.
From our view, the breach was caused by at least four issues – one process and three technical.
The process issue is that the partner account is created in 24-48 hours without much verification. However, this isn’t an issue if the following three technical issues are fixed.
The first technical issue is that when a partner account is created, no linked entitlement or form of authorization is provided to allow that partner to search and work with specific service tags. This is particularly egregious since the data isn’t only details of the hardware—it provides, among other things, the customer's physical address.
The second is the lack of protection against automation. 5000 requests/minute for 3 weeks from an account without rate limiting. Even if 5 accounts are used, that is 1000/requests/minute/account.
This brings us to the third issue – lack of visibility and alerting. The IT security teams were not alerted to this obvious attack behavior. There are two possible reasons for this:
There was no logging and alerting for the APIs behind the portal.
This type of data access is common and did not cross their alert thresholds.
From the looks of it, this web interface has an API. As a research note from Forrester stated a few years ago, “APIs are the new storefront, but security has not kept up.” First, no authorization was enabled for the endpoints – allowing anyone to see every customer’s data and personal information. Next, no rate-limiting was in place to protect the server from overloads or data exfiltration. There is a very good chance that the protectors of the app did not know there was an API behind it that was to be protected (Shadow API) – this would be both a process failure and a technical security failure.
There were no safeguards – process-wise or technically – against new accounts performing such a large number of requests. There was no alerting (though Dell claims otherwise), and this allowed attacker persistence for THREE WEEKS WITH 5000 REQUESTS/MINUTE!@!@!@?!@!?!??!
(Pardon my indignation – it’s been a long day, and the full import of this breach is just sinking in, coming on the heels of the 23andMe and Roku breaches.)
Barracuda can help.
Today’s article is sponsored by…. Barracuda Application Protection! Barracuda Application Protection is a comprehensive Web Application and API Protection platform that is easy to use and manage. In this case, it provides the following relevant protections –
Machine learning-powered API Discovery uses live traffic data to identify API endpoints (Shadow or otherwise) and then automatically turns on protection for the discovered API endpoints.
Advanced Rate Limiting and Tarpits that can work on both a per-IP and a per-device setting. The per-device setting is very useful when your clients sit behind a NAT and use multiple devices.
Authorization enforcement down to the parameter level, with integrations with JWT and Client certificates. This includes the ability to enforce VBAAC and ABAC.
Machine Learning powered Account Takeover Protection with multiple layers of protection, including Credential Stuffing protection (for known breached accounts) and Privileged Account Protection (for accounts that are newly taken over.)
Machine Learning powered Advanced Bot Protection that identifies and blocks the most advanced bots, including scrapers.
Detailed Logging and Alerting, including integrations with SIEM/SOAR/XDR solutions like Azure Sentinel, Splunk, SumoLogic, Barracuda XDR, and more.
Barracuda offers complete application protection and the industry’s most comprehensive cybersecurity platform that defends all attack vectors with real-time threat intelligence and incident response. Visit our website to see how we defend email, networks, applications, and data.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.