Un análisis más detallado del ransomware Fog
El ransomware Fog surgió en abril de 2024 como una sofisticada ciberamenaza que combinaba el cifrado rápido con tácticas de doble extorsión. Los actores de amenazas de Fog inicialmente atacaron a instituciones educativas mediante cuentas VPN comprometidas. Pronto ampliaron su alcance a agencias gubernamentales y sectores empresariales. A partir de febrero de 2025, los cinco principales sectores afectados por Fog son los servicios empresariales, la tecnología, la educación, la manufactura y el gobierno. La mayoría de las víctimas de Fog están ubicadas en los Estados Unidos.
Los investigadores sospechan que los actores de amenaza Fog operan desde Rusia u otras naciones exsoviéticas, ya que evitan de manera conspicua dirigirse a los países de Europa del Este y a la República Popular China. En un ataque de 2024, los investigadores rastrearon el origen de la dirección IP relacionada con Fog hasta Moscú.
¿Grupo o variante?
Los analistas han sido cuidadosos al distinguir el ransomware Fog como una variante, en lugar de un grupo de amenazas. No parece haber evidencia alguna de una operación centralizada detrás del uso de Fog. Puede ser utilizado por diferentes actores de amenazas para llevar a cabo ataques, y los desarrolladores están separados de aquellos que realizan las intrusiones.
Las filiales de Ransomware-as-a-Service (RaaS) también operan por separado de los desarrolladores de ransomware, pero siempre hay evidencia de una jerarquía organizativa o una separación de funciones detrás del software. Existen reglas y estructuras de pago para los afiliados. No podemos considerar a Fog una operación de RaaS porque no encaja en esa descripción.
Tampoco podemos descartar la posibilidad de que Fog se utilice o se haya tenido la intención de usarlo en una operación de RaaS. Su diseño modular permite a los atacantes controlar qué se cifra, el ritmo del ataque, el alcance del cifrado y el contenido de la nota de rescate. Es posible que se haya desarrollado con una operación RaaS en mente.
Aunque Fog no parece ser una única organización, sí se ajusta a los parámetros comúnmente entendidos de un «grupo de actores de amenazas». Los atacantes Fog comparten infraestructura y malware; tienen tácticas, técnicas y procedimientos (TTPs) comunes, y utilizan correos electrónicos de phishing, notas de rescate y charlas de negociación similares en todos los ataques. También existe un sitio de filtraciones y un portal de negociación de la marca Fog, lo que significa que estos actores de amenazas están coordinando cómo se comunican con las víctimas.
También se ha observado a los actores de niebla comunicarse durante los ataques utilizando servidores de mando y control (C2C) y canales de comunicación cifrados.
Niebla por los números
Basándose en los datos disponibles, los analistas han calculado las siguientes métricas:
- Número de víctimas denunciadas públicamente: 189 a fecha de abril de 2025
- Demanda inicial media de rescate: 220 000 $
- Pago medio de rescate: 100 000 dólares
Se desconoce la cantidad recaudada por Fog. Si todas las víctimas denunciadas públicamente pagaran el pago medio del rescate, eso sería de 18,9 millones de dólares. Sabemos que no todas las víctimas pagan el rescate, y no todos los incidentes se denuncian. Una encuesta reciente encontró que el 86 % de las organizaciones (a nivel mundial) han pagado demandas de rescate en el último año, lo cual es interesante, pero probablemente no sea aplicable a las víctimas de Fog.
No hay evidencia de que los actores de amenaza Fog estén motivados por algo más que el dinero. No han declarado lealtad a ningún estado-nación ni han mostrado apoyo a ninguna ideología o causa.
Cómo funciona Fog
La niebla normalmente se propaga a través de uno de los siguientes métodos de acceso inicial:
- Cuentas VPN comprometidas de SonicWall: Estas cuentas suelen comprarse a través de un corredor de acceso inicial (IAB), pero también pueden ser robadas directamente mediante campañas de phishing.
- Explotación de vulnerabilidades: El grupo ataca activamente el software sin parches, especialmente Veeam copia de seguridad & Replication (CVE-2024-40711)
- Campañas de phishing: los actores de amenazas de Fog utilizan campañas de phishing para desplegar el cargador de ransomware. Estos correos electrónicos suelen presentarse como una solicitud de actualización de VPN, una consulta sobre facturas impagadas y una notificación de cambio en la política de recursos humanos (RRHH). Los archivos adjuntos actúan de manera diferente, pero todos resultan en intentos de descargar el cargador de ransomware Fog.
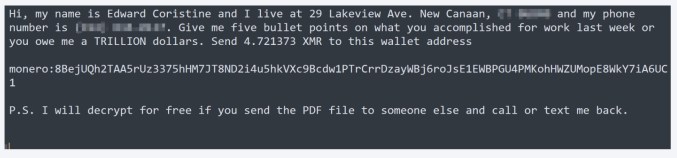
Las campañas de phishing recientes han empleado correos electrónicos de phishing con un archivo ZIP adjunto que contiene un acceso directo LNK malicioso. El archivo LNK ejecuta un comando que descarga un script de PowerShell llamado "stage1.ps1" desde un dominio controlado por un atacante. El script luego descarga varios payloads y archivos de soporte. Las notas de rescate asociadas a estos ataques han añadido insulto a la injuria al burlarse de las víctimas con referencias a Edward Coristine y al Departamento de Eficiencia Gubernamental de EE. UU. (DOGE).
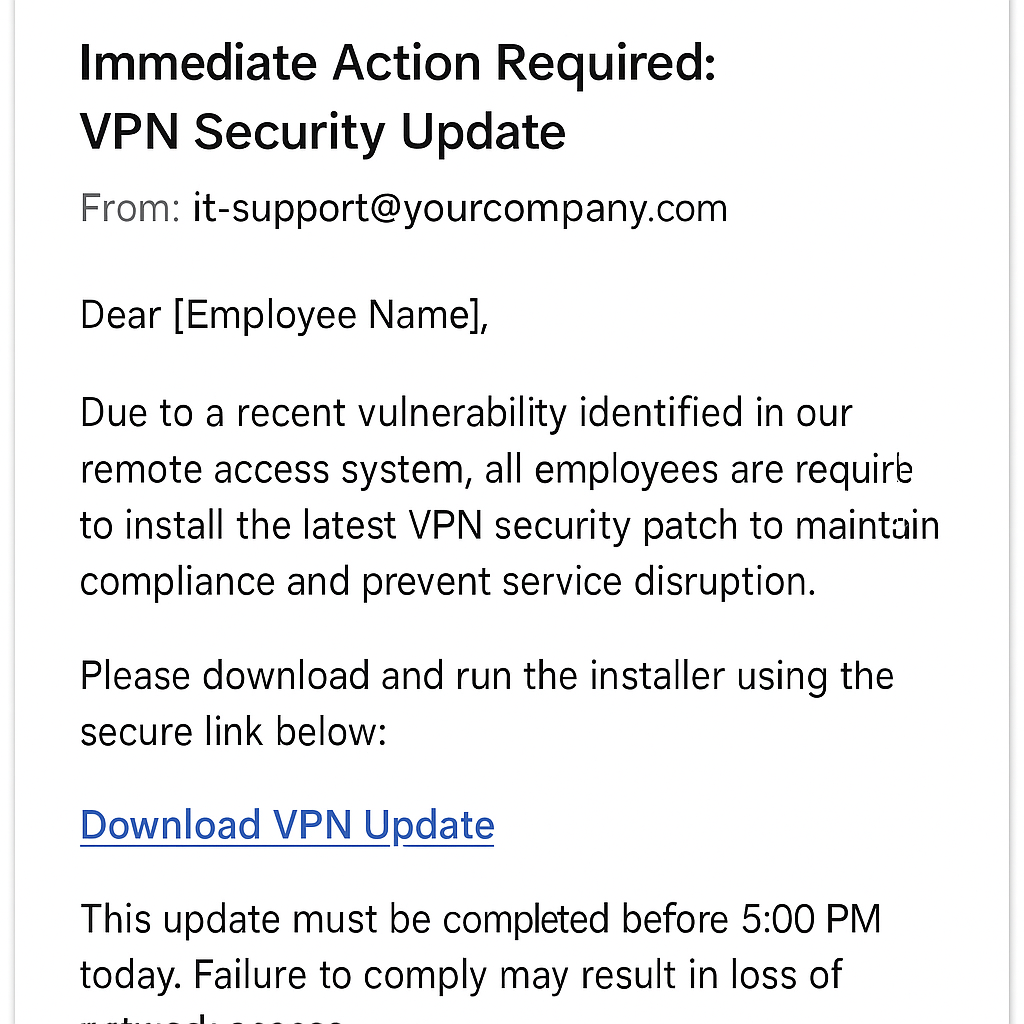
Correo electrónico de phishing de niebla: actualización falsa de VPN (maqueta)
Los investigadores han determinado que no hay una afiliación real entre el ransomware Fog y DOGE.
Una vez dentro del sistema, Fog inicia de inmediato el reconocimiento del sistema e intenta establecer persistencia modificando las configuraciones del sistema e implementando scripts adicionales que mantienen el malware activo tras un reinicio del sistema. El siguiente paso es obtener el control administrativo mediante el uso de herramientas como Mimikatz y técnicas como el volcado de memoria de LSASS y los ataques de retransmisión NTLM. Fog también implementará medidas anti-recuperación, como cifrar las copias de seguridad y eliminar las copias de sombra del volumen.
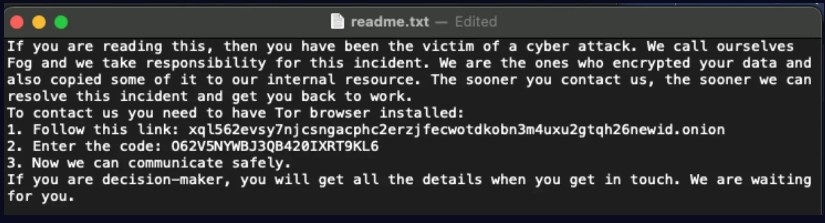
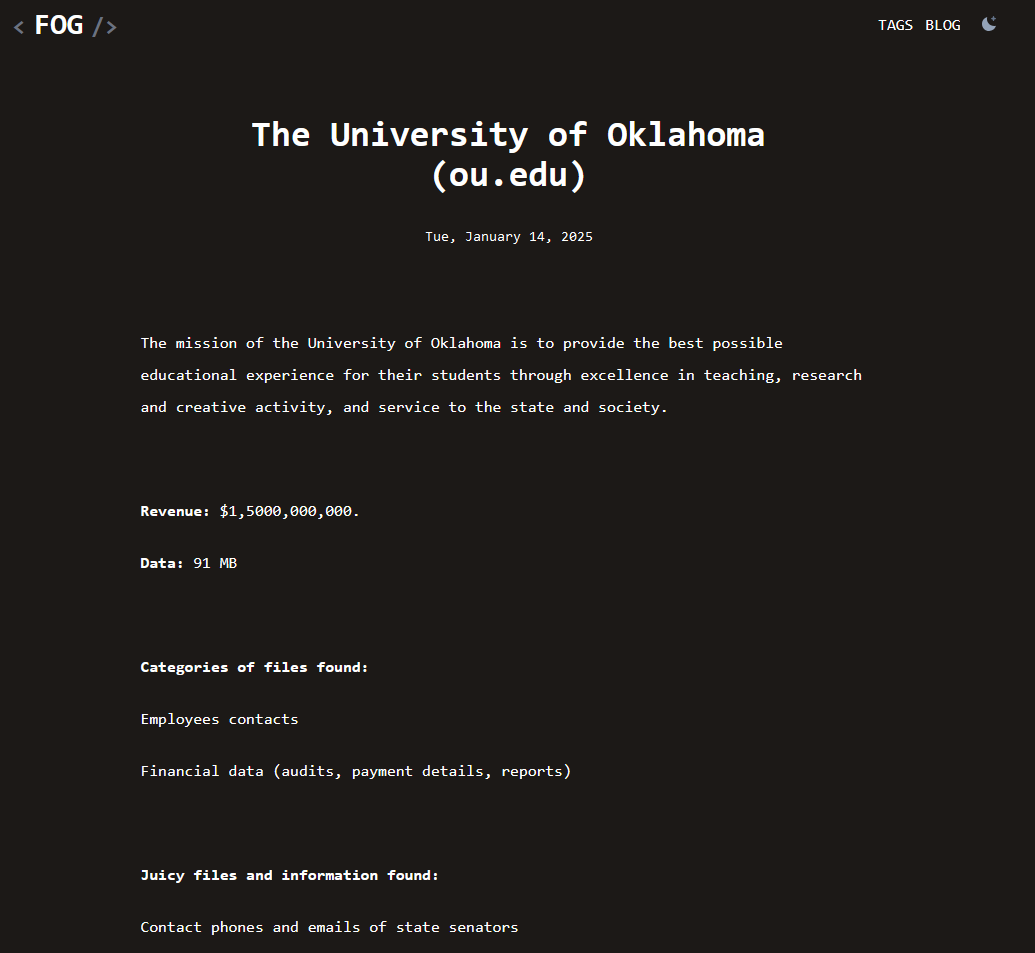
El ataque avanza con movimiento lateral y exfiltración de datos. Los actores de fog utilizan el servicio en la nube de conocimiento cero Mega.nz para almacenar datos robados antes de cifrar la red. Esto establece el esquema de doble extorsión. Cuando esto se complete, Fog cifrará documentos, bases de datos, copias de seguridad y cualquier otro dato operativo crítico. Las extensiones .fog, .Fog, o .FLOCKED se añaden a los archivos cifrados, y notas de rescate llamadas "readme.txt" se distribuyen a través de la red. La información de la víctima se añade al sitio de filtraciones de Fog.
Después del ataque
Las tácticas de negociación siguen las mismas que las de otros grupos.
Si desea que sus datos sean completamente descifrados y que los archivos que robamos sean eliminados de nuestra fuente, tendrá que pagar una tarifa. También podremos proporcionarle un informe de seguridad y explicar cómo logramos acceder. (source)
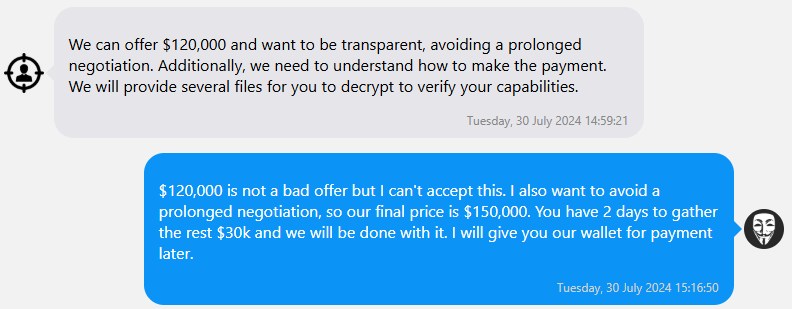
Fog comienza con una alta demanda de rescate y se comprometerá a aceptar una cantidad menor si es aceptable.
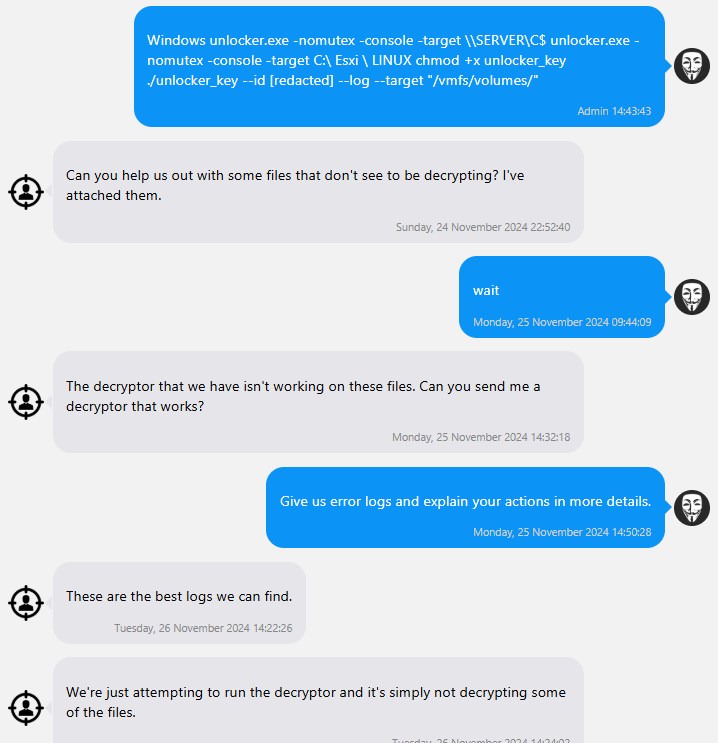
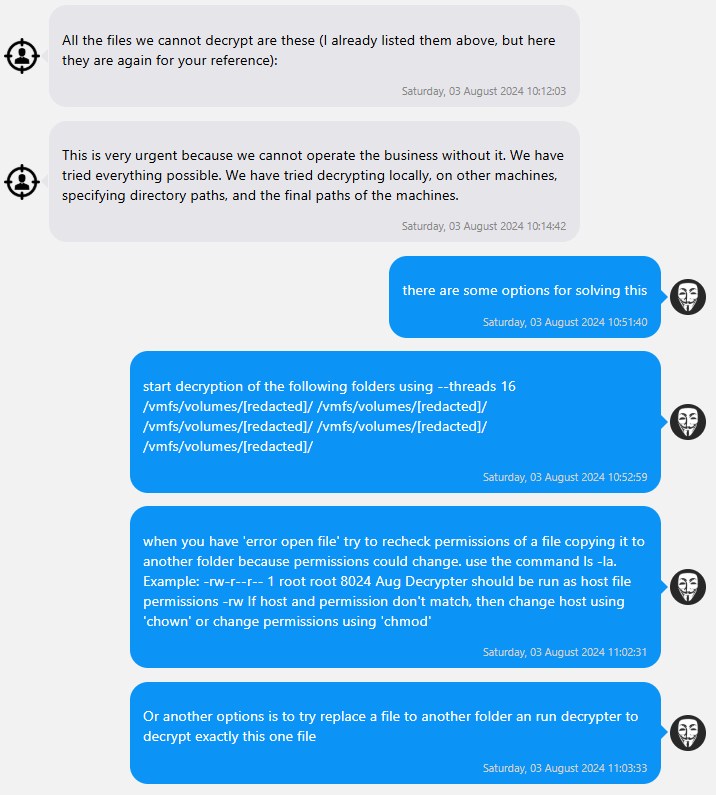
Tras el pago, Fog enviará las claves de descifrado y confirmará la eliminación de los datos robados. En dos de los chats disponibles aquí, la víctima tuvo dificultades para recuperarse y tuvo que resolver problemas con el actor de la amenaza:
El informe de seguridad prometido por Fog probablemente no sea útil para las víctimas que ya siguen las prácticas recomendadas.
Se obtuvo acceso a su red mediante un correo de phishing. Su personal debería ser más vigilante al descargar y abrir archivos desconocidos. Le recomendamos que implemente las siguientes medidas para proteger su red corporativa: 1) Hacer cumplir el uso de contraseñas en los administradores locales y de dominio. Complicar la política de grupo sobre contraseñas para todos los usuarios; 2) Usar el grupo «Usuarios protegidos»; 3) Usar la gestión centralizada de la protección antivirus; 4) Informar a los usuarios de que no abran correos electrónicos y archivos sospechosos; 5) Actualizar el software y el sistema operativo a las versiones actuales; 6) Configurar la delegación de permisos en Active Directory; 7) Instalar una aplicación para supervisar la actividad en Active Directory; 8) Usar VMware Esxi ver. 7,0 o más reciente. Nuestro equipo garantiza que cualquier dato extraído de su red no será divulgado, vendido ni publicado. Por supuesto, este diálogo también se mantendrá confidencial. (source)
El lenguaje es similar al de los «informes de seguridad detallados» proporcionados por Akira.
Amigos y familiares
Fog apenas tiene un año, pero los investigadores sospechan que sus operadores son actores experimentados de amenazas de ransomware. Un análisis de las intrusiones de Fog a través de cuentas VPN comprometidas de SonicWall muestra que solo el 25 % de las intrusiones estaban vinculadas directamente con Fog. El 75 % restante de las intrusiones de Fog estaban vinculadas al ransomware Akira, lo que sugiere colaboración e infraestructura compartida. Fog y Akira también utilizan herramientas y exploits similares y son conocidos por sus técnicas de cifrado rápido.
Fog también ha sido vinculado al ransomware Conti a través de carteras de criptomonedas compartidas. Los investigadores vincularon Akira con Conti en 2023, por lo que el vínculo con Conti no es sorprendente, pero es digno de mención para los investigadores y analistas. Aquí tiene un resumen de alto nivel de la familia Conti:
- Ryuk: agosto de 2018 - principios de 2022. Evolucionó a partir de Hermes y es el precursor directo de Conti.
- Conti: diciembre de 2019 - junio de 2022. Se cerraron y se fragmentaron en varios grupos.
- Karakurt: Surgió en junio de 2021 y sigue activo en 2025. Escisión de Conti.
- Quantum: Surgió en agosto de 2021 y sigue activo en 2025. Rebranding de MountLocker con vínculos a Conti.
- BlackByte: Surgió a mediados de 2021 y sigue activo en 2025. Afiliado de Conti.
- Zeon: enero de 2022 - septiembre de 2022. Precursor directo de Royal con conexiones a Conti.
- Royal: septiembre de 2022 - mediados/finales de 2023. Rebranding de Zeon que evolucionó a BlackSuit.
- Black Basta: Surgió en abril de 2022 y sigue activa en 2025. Escisión de Conti.
- Akira: Surgió en marzo de 2023 y sigue activa en 2025. Estrechamente vinculado a Conti.
- BlackSuit: Surgió a mediados de 2023 y está activo desde 2025. Rebranding o evolución de Royal.
- Niebla: surgió en abril de 2024 y está activa desde 2025. Vinculado a Akira y Conti.
Conti fue observado por primera vez en diciembre de 2019 y estaba completamente offline para junio de 2022. Examinar el ransomware Fog en este contexto destaca el hecho de que nuevo no significa inexperto. La experiencia criminal, los avances en el código y las técnicas de ataque se trasladan fluidamente entre estos grupos.
Ataques destacados
En junio de 2024, Darktrace observó múltiples ataques de ransomware Fog en los entornos de los clientes, incluido uno que tardó menos de dos horas desde el acceso inicial hasta el cifrado completo de los archivos. Este fue el primer ataque que demostró la velocidad y la sofisticación de Fog. Los métodos de ataque incluyeron intentos de autenticación NTLM salientes hacia otro dispositivo interno, que luego se utilizó para establecer una conexión remota a un servidor Windows que ejecutaba Hyper-V. Este ataque fue notable por su rapidez y eficiencia, y es uno de los primeros indicadores de que múltiples actores de Fog colaboran en tiempo real.
Uno de los ataques más interesantes ocurrió en agosto de 2024, cuando Fog atacó a una empresa de servicios financieros. Los intrusos iniciaron sesión mediante una cuenta VPN utilizando credenciales robadas. Los equipos de seguridad rastrearon la IP de este intruso hasta Moscú, proporcionando a los investigadores la primera evidencia de los orígenes rusos de Fog. El ataque también fue uno de los primeros en dirigirse a un sector diferente al de la educación. El ataque fue detectado antes del cifrado y, por lo tanto, no tuvo éxito.
Los actores de amenazas de Fog dirigieron sus ataques a los ministerios del Gobierno de Brasil en julio de 2023, lo que resultó en el compromiso de nueve ministerios, la Casa de la Moneda de la nación y su agencia contra el lavado de dinero. Los atacantes exigieron 1,2 millones de dólares, pero no hay evidencia de que se haya pagado un rescate. El incidente todavía está bajo investigación.
Este ataque fue reivindicado por Fog en la nota de rescate y la víctima está listada en el sitio de filtraciones de Fog, pero ocurrió nueve meses antes de que Fog surgiera como una amenaza. Esto es posible porque la aparición de una amenaza comúnmente se refiere a cuando una amenaza es observada y reconocida públicamente. Puede haber un retraso significativo entre el primer ataque y la primera observación por parte de la industria o de un investigador. Después de que surge una amenaza, los investigadores comienzan a vincular la nueva amenaza con ataques anteriores. Esto se conoce como «vinculación retrospectiva».
Defiéndase
La defensa contra Fog y otros actores de amenazas de ransomware comienza con las mejores prácticas y una seguridad en capas. Comience con sistemas de autenticación sólidos que incluyan la autenticación multifactorial (MFA) y el acceso de zero trust. Mantenga un sistema sólido de gestión de parches y cierre las vulnerabilidades técnicas, como las cuentas VPN no utilizadas.
Puede restringir el movimiento de los intrusos segmentando las redes y aislando los datos confidenciales y los sistemas de copia de seguridad. El acceso de Zero Trust permite la microsegmentación al aislar las cargas de trabajo individuales y aplicar una verificación continua a través de los usuarios y dispositivos.
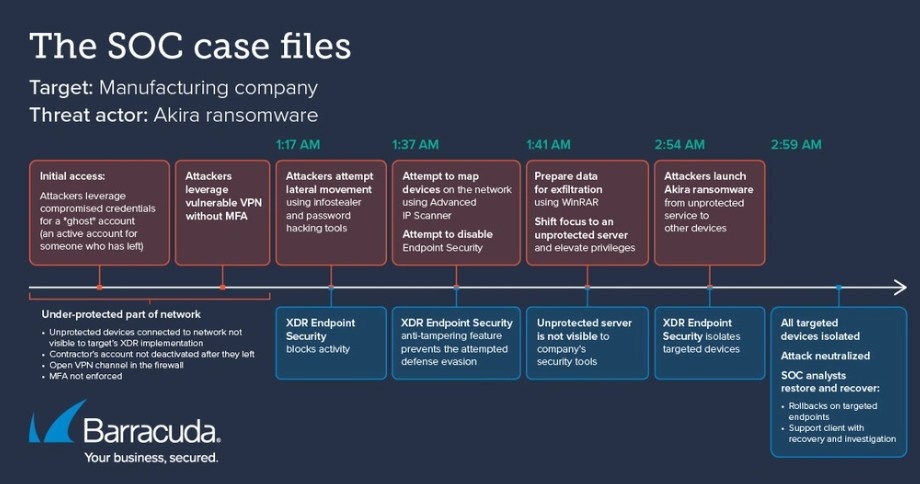
Considere añadir seguridad avanzada a su red con Barracuda Managed XDR. Esta solución puede identificar y detener las actividades maliciosas de Fog antes del cifrado y la exfiltración de datos. Consulte nuestro blog aquí para un desglose minuto a minuto de cómo nuestro equipo detuvo un ataque del ransomware Akira.
Utilice una solución de copia de seguridad de primer nivel para proteger sus datos, los estados del sistema y las configuraciones de los dispositivos, las bases de datos, las máquinas virtuales, los datos de Entra ID, los despliegues de SharePoint y Microsoft 365, y cualquier otra cosa que no pueda permitirse perder. Barracuda ofrece múltiples soluciones de protección de datos para entornos locales, en la nube e híbridos.
Y, por último, mantenga un programa actualizado de formación en concienciación sobre la seguridad para los empleados. Todos los usuarios de la red deben saber cómo reconocer los correos electrónicos sospechosos. Invierta en un programa de formación que pueda simular ataques con muestras de las campañas de phishing más recientes.
Barracuda puede ayudarles
Las soluciones de seguridad de Barracuda están impulsadas por IA y la inteligencia de amenazas global. Nuestras soluciones defienden ferozmente todos los vectores de ataque con protección frente a amenazas avanzadas y Respuesta ante incidentes que se puede orquestar en todas las soluciones. Visite nuestro sitio web para programar una demostración y ver cómo puede ayudar a proteger su entorno.

Informe sobre brechas de seguridad del correo electrónico 2025
Principales hallazgos sobre la experiencia y el impacto de las brechas de seguridad del correo electrónico en organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Informe sobre perspectivas de clientes MSP 2025
Una perspectiva global sobre lo que las organizaciones necesitan y desean de sus proveedores de servicios gestionados de ciberseguridad.