Black Basta’s nasty tactics: Attack, assist, attack
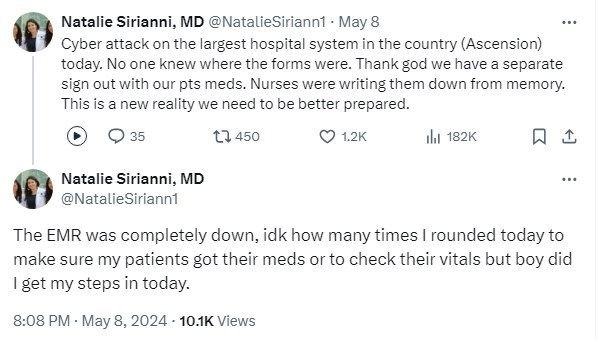
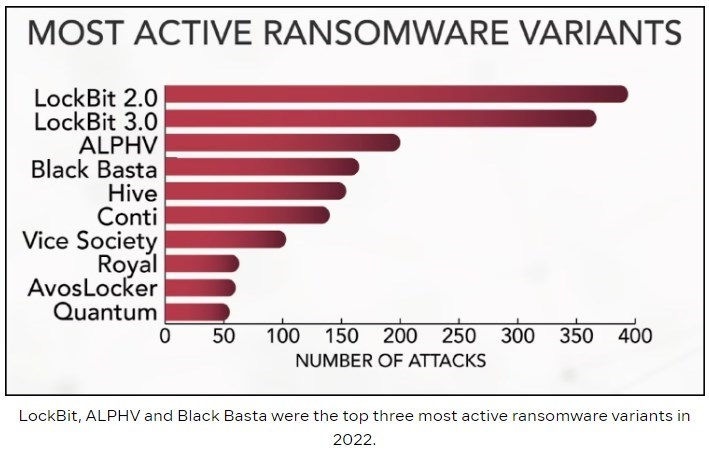
Black Basta is one of those ransomware clusters that doesn’t mess around. The threat emerged in April 2022 and claimed nearly 100 victims in seven months. It is known for its sophisticated tactics and attacks across multiple sectors. One of the most recent victims is the Catholic healthcare system Ascension, which announced its discovery of the attack on May 9, 2024. Black Basta was able to disrupt 140 Ascension hospitals across 19 states and Washington DC. Phones and computer systems went offline, and staff were forced to switch to paper systems.
Several Ascension facilities canceled non-emergency procedures and appointments, and several hospitals are diverting ambulances and emergency services to other facilities “in order to ensure emergency cases are triaged immediately.”
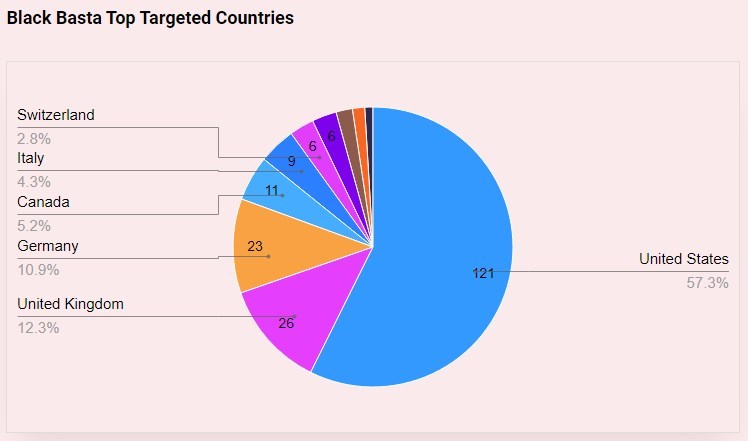
On May 10, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA) to provide background information and technical details on Black Basta. The advisory warns Black Basta threat actors have businesses and critical infrastructure in North America, Europe, and Australia.
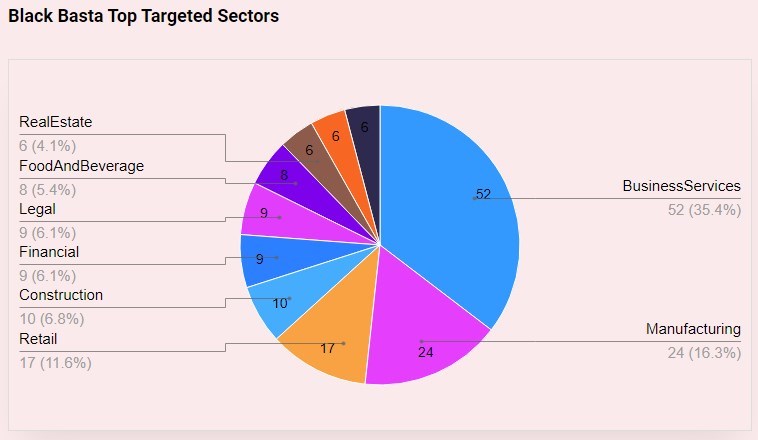
As of May 2024, Black Basta affiliates have affected over 500 organizations globally, including 12 out of 16 critical infrastructure sectors in the U.S. Black Basta also targets many economic sectors.
Another high-profile victim currently recovering from this group is Synlab Italia, a medical diagnostic group that operates hundreds of locations across Italy. The group isolated its network and canceled all laboratory analysis and sample collection services. Black Basta listed Synlab on its leak site in early May 2024.
And there are several other notable victims:
-·Capita (UK technology outsourcer)
--ABB (Swiss industrial automation company)
--Dish Network (U.S. television provider)
--Raleigh Housing Authority (U.S.)
--Deutsche Leasing AG (Germany)
--Twin Towers Trading, Inc. (U.S.)
--Van der Ven Auto’s B.V. (Netherlands)
Who is Black Basta?
The exact origins of the group are unclear, but there are several indications that the group operates out of Russia or another country in Eastern Europe. The group’s ransom notes and other communications are in Russian or contain pieces of the Russian language. It’s also known to operate during common business hours in Russian time zones. Several other factors, like Black Basta’s ransom payment channels and tactics, techniques, and procedures (TTPs) are like other groups with ties to Russian cybercriminal networks.
The name ‘Black Basta’ doesn’t seem to mean anything. Dictionary.com tells us that “Basta is an Italian and Spanish word meaning “Stop!” or “That’s enough!””, so the phrase means “black enough” or “black stop” or something else that doesn’t translate well enough to articulate in English. Experts think it’s meant to project an image of stealthy disruption, and I’m just going with that.
When it comes to Black Basta attacks, it’s more accurate to think of this threat as a cluster rather than a group. The Black Basta operators develop the ransomware and manage the payments, leak site, and other infrastructure, but the affiliates carry out the attacks. Black Basta is a closed ransomware-as-a-service (RaaS) group that does not advertise their service or openly request affiliates. The threat actor carefully seeks affiliates that have had success in ransomware attacks or malware development. This selection process contributed to their rapid success in 2022.
The recruitment process has contributed to speculation that the group may be state-sponsored. Researchers noted in 2023,
“Chat logs for Black Basta now in the public domain show:
--Technical assistance being offered
--Cryptocurrency tutorials
--Friendly interactions with clients
There are even promises of forensic reports, detailing the vulnerabilities that have been used to gain access in the first instance.”
This sophistication suggests that Black Basta is a stable operator, which would make it attractive to many potential affiliates. As far as we know, they’re strictly motivated by financial gain, and there is no state or ideological affiliation.
Black Basta attacks are all about the money
Between April 2022 and November 2023, about 35% of Black Basta operators paid a ransom, and the threat actor collected more than $107 million in payments. Affiliates were paid 14% of those ransoms, and Qakbot malware operators were paid about 10% of the ransom collected from attacks where Qakbot was used.
The typical affiliate uses common techniques like stealing credentials through phishing attacks, but Black Basta operators also purchase access from Initial Access Brokers (IABs). An IAB is a threat actor who specializes in finding a way into a network and then selling his access to another party. By using these brokers, Black Basta threat actors can begin their attacks right away.
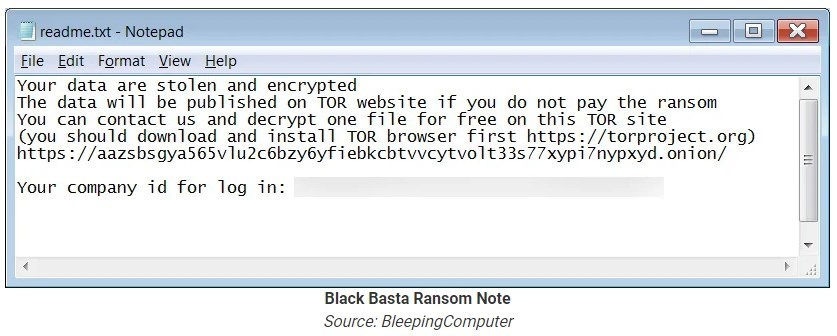
The attacker often uses Qakbot, Emotet, and Cobalt Strike to infiltrate a system, escalate privileges, and move laterally within the network. He’ll set up command-and-control (C2) servers to manage data exfiltration and ransomware deployment. The attack delivers a ransom note demanding payment in cryptocurrency, with instructions to visit the Black Basta dark web portal where they can communicate with the attackers and receive decryption tools upon payment.
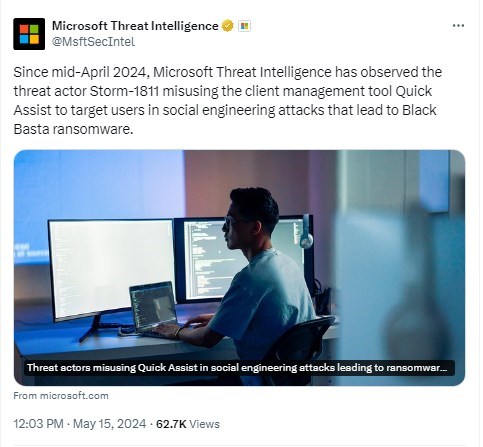
Since April 2024, a threat actor known as Storm-1811 has been observed using a new procedure to gain access to high-value networks. These attacks begin with a massive phishing attack sent to employees of the target company. The attack floods the inboxes and leaves employees frustrated and overwhelmed. While this phishing/spam attack is underway, Storm-1811 launches a voice phishing (vishing) attack in which the caller poses as tech support. If successful, the caller tricks the employee into providing remote access to the system via Microsoft Quick Assist.
Attack, assist, attack
Storm-1811 has also been observed exploiting AnyDesk when Quick Assist is not available. AnyDesk is a third-party remote management application, and like Microsoft Quick Assist, it allows tech support to assist the end-user with IT issues.
Once the threat actor has control via the remote assistance tool, he will execute scripts that install the malicious payloads that will lead to the Black Basta ransomware attack. Some of these scripts appear to be fake spam filter updates that require the employee to enter his username and password. This piece is a phishing attack to steal user credentials.
Storm-1811 will then turn to a hands-on-keyboard attack and manually begin reconnaissance and lateral movement. This is called “domain enumeration,” in which “the threat actor gathers detailed information about a network’s structure, resources, and security controls, specifically within the context of a Windows Active Directory (AD) environment.” In other words, the threat actor works to extend his attack surface in the domain. When ready, he’ll begin data exfiltration and deploy the ransomware.
This combination of traditional spam/phishing, vishing/social engineering, and remote access appears to be a new attack chain based on carefully crafted pretexting. The attack may also be the first use of Microsoft Quick Assist as a network infection tool by a known threat actor. Quick Assist is available through the Microsoft Store and can be blocked or disabled at any time.
Black Basta family tree
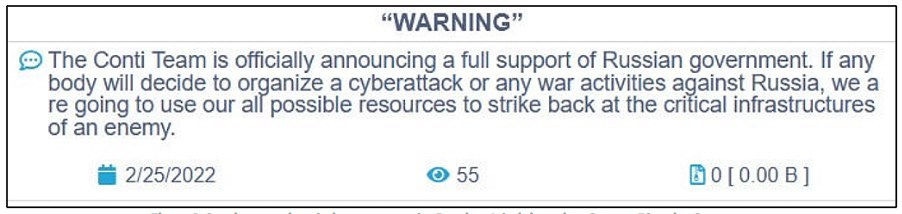
Black Basta has been linked to several notable threat actors and groups, primarily through similarities in tactics, techniques, and procedures (TTPs), as well as through direct operational overlaps. It is widely believed to be another rebrand or offshoot of the Conti ransomware group. Conti went dark in May 2022, probably because of internal conflicts caused by its declaration of support for Russia.
It makes sense that Conti threat actors would splinter and rebrand and continue to use old methods and resources.
Elliptic blockchain analysts “traced Bitcoin worth several million dollars from Conti-linked wallets to those associated with the Black Basta operator.” Both Conti and Black Basta use Russian cryptocurrency exchange Garantex to launder their ransoms.
Researchers have also linked Black Basta to threat actor FIN7, also known as Carbanak and many other names throughout the years. FIN7 has worked with many ransomware operators over the years, including REvil, CLop, Blackmatter, ALPHV, and Darkside (Colonial Pipeline).
We also know that QakBot is frequently used by Black Basta to gain initial access to facilitate lateral movement within compromised environments. QakBot, also known as Qbot, Pinkslipbot, and Quakbot, is a multipurpose malware platform that started its life in 2007 as a simple banking Trojan. Ongoing development and enhancements turned it into a downloader, worm, backdoor, keylogger, and botnet. It can also exploit network shares and vulnerabilities, which gives it the lateral movement capabilities used by Black Basta. QakBot was dismantled by law enforcement in August 2023, but variants of Qakbot returned later that year.
These relationships don’t tell us who Black Basta is, but they reveal the interconnectedness of the cybercrime ecosystem. Rival groups use the same brokers, the same infrastructure, and sometimes the same affiliates.
Protect yourself
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published this advisory that includes indicators of compromise (IoC) and mitigation procedures. You should review these for detailed information on the Black Basta threat. Also, make sure you’re following the standard best practices of regular backups, timely patch management, email security, network segmentation, and security awareness training.
Barracuda offers complete ransomware protection and the industry’s most comprehensive cybersecurity platform. Visit our website to see how we defend email, network, applications, and data.

Informe sobre brechas de seguridad del correo electrónico 2025
Principales hallazgos sobre la experiencia y el impacto de las brechas de seguridad del correo electrónico en organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Informe sobre perspectivas de clientes MSP 2025
Una perspectiva global sobre lo que las organizaciones necesitan y desean de sus proveedores de servicios gestionados de ciberseguridad.