The rise and fall of LockBit ransomware
An international task force has seized a significant chunk of the infrastructure belonging to the ransomware group LockBit. This is a major disruption to LockBit’s criminal enterprise, rendering it “effectively redundant” according to Graeme Biggar, director general of the National Crime Agency (NCA). The “takedown” of LockBit was announced by Europol and the U.S. Federal Bureau of Investigation (FBI) in separate press conferences. The FBI’s Cyber Deputy Assistant Director Brett Leatherman said the operation disrupted LockBit's “front- and back-end infrastructure in the U.S. and abroad” and hindered LockBit’s ability to sting again.
Officials are also reaching out to known LockBit victims to distribute decryption keys and other available assistance. If you are a victim of LockBit or other ransomware, you can find assistance by visiting the FBI website for LockBit victims or the international No More Ransom portal.
Operation Cronos
Operation Cronos is an international effort to target and disrupt LockBit ransomware. There are ten task force member agencies and another four agencies that were not members but assisted in the operation. These international agencies are detailed in the Europol and FBI announcements. The FBI began targeting LockBit in 2021 with a multi-phase campaign to eliminate this group. U.S. law enforcement and intelligence agencies targeted the LockBit operators, their finances, their communications, their malware, and the supporting infrastructure. Once this was accomplished, the next step was the seizure of this entire infrastructure and the criminal charges against the threat actors.
The current known results of Operation Cronos are briefly summarized here:
- Operation Cronos seized 34 servers in total, including four in the U.S.
- Two LockBit affiliates have been arrested and charged by the Department of Justice. Three more affiliates will have charges announced soon.
- The US Office of Foreign Assets Control (OFAC) imposed sanctions on two LockBit threat actors responsible for malicious cyber-enabled activities.
- Over 1,000 decryption keys have been seized and will be distributed to victims.
- The U.S. Department of State is offering a reward of up to $15 million via the Transnational Organized Crime Rewards Program for anyone with information about LockBit associates.
- More than 200 LockBit-affiliated crypto-wallets have been seized.
The long life of LockBit
LockBit is an old group that was operating as ABCD ransomware when it was first observed in 2019. It rebranded to LockBit and adopted the Ransomware-as-a-Service (RaaS) model in 2020. It's an interesting group because it operated under a business model that included ongoing investments in operations, proactive recruitment, and public relations. Here’s a rough timeline of LockBit’s notable events:
2021:
June - LockBit 2.0 (aka LockBit Red) is observed in the wild.
October - LockBit 2.0 adds features that target Linux and VMware ESXi.
2022:
March - LockBit 3.0 (aka LockBit Black) is observed in the wild.
August – LockBit operators add Distributed Denial of Service (DDoS) attacks to their operations, effectively creating a triple extortion threat.
September – LockBit 3.0 builder is leaked to the public, and non-LockBit threat actors begin using the leaked code to start their own operations.
September – LockBit offers to pay people to get LockBit tattoos and upload pictures to social media.
2023:
January - LockBit Green is released. This version includes source code from Conti ransomware.
February – Canada's cyber intelligence agency describes LockBit as a “prolific ransomware group with ties to Russia” and calls it an “enduring threat” to the state.
March – LockBit claims to have breached the City of Oakland, though this was not considered a credible claim at the time.
April - LockBit releases ransomware that targets MacOS.
June - LockBit is said to have been the most deployed ransomware variant across the world in 2022.
June – LockBit and 8Base ransomware are identified as the top two threat actors against industrial targets.
August – LockBit operators contribute prize money in the Russian forum writing competitions, which are intended to develop and recruit threat actors.
November – LockBit’s RaaS compensation scheme is changed to force higher ransom demands by affiliates.
December – LockBit actively recruits developers and affiliates of BlackCat/ALPHV and NoEscape ransomware groups.
December – LockBit publicly apologizes for an attack on a children’s hospital
In the first half of 2023, researchers found the average lifespan of a ransomware threat actor to be 262 days, and the median lifespan to be 167 days. At the time of that report, LockBit 3.0 had been operating for 367 days.
Jon Dimaggio has written extensively on LockBit operations. In January 2024 he described why LockBit has been around for so long:
“They are the most notorious ransomware group, because of sheer volume. And the reason for their success is that the leader is a good businessman.
…
They made a point-and-click ransomware that anyone could use, they update their software, they’re constantly looking for user feedback, they care about their user experience, they poach people from rival gangs. He runs it like a business, and because of that, it is very, very attractive to criminals.”
Law enforcement officials and security researchers have also credited LockBit’s longevity to this business-like approach.
Versions and targets
The story of LockBit is also revealed in the capabilities and targets of their malware. There are four versions of LockBit commonly referenced by researchers and media:
LockBit is the original version of the ransomware that appeared in 2019. It was notable for its automated ability to deploy encryption in under five minutes and spread rapidly within a network. Key features of this version include:
- Strong encryption algorithms made the files on the infected systems inaccessible to the victim.
- Lateral movement through the network infected other systems and devices connected to the same network.
- After encrypting files, LockBit displayed a ransom note demanding payment in exchange for a decryption key.
LockBit 2.0 was “officially” released in July 2021 and was a significant improvement over the previous version. This version could exploit Active Directory group policies to automatically encrypt Windows domains. A few months after release, 2.0 added the capability to target Linux hosts and ESXi servers and encrypt VMware images hosted on these platforms. Other key features:
- LockBit 2.0 introduced a "double extortion" tactic using StealBit for data exfiltration. This allowed LockBit operators to steal sensitive data from infected systems, and then threaten to release this data publicly if the ransom is not paid. Double extortion tactics increased the pressure on victims to pay the ransom rather than restore from backup.
- Improved encryption techniques made it more difficult to decrypt files without the decryption key.
- Evasion and stealth capabilities were improved, making it harder for security software to detect and block the ransomware.
LockBit 3.0 was launched in late June 2022. This version further increased encryption speed and introduced anti-analysis techniques, password-only execution, and command line augmentation. With this version, LockBit operators added a bug bounty program to encourage the reporting of vulnerabilities in exchange for financial rewards.
- 3.0 employs some features known to be used by BlackMatter and Alphv (BlackCat) ransomware.
- LockBit 3.0 uses even stronger encryption algorithms, making it virtually impossible to decrypt files without the decryption key.
- Stealth capabilities are improved significantly, making it even harder for security software to detect and block the ransomware.
- 3.0 adds capabilities to delete log files, empty the recycle bin, and change the host system’s wallpaper and icons.
- DDoS capabilities give LockBit the ability to threaten triple extortion.
LockBit Green was released in January 2023 and incorporated source code from Conti ransomware. It targeted Windows environments and was specifically modified to target cloud-based services.
Each version of LockBit improved existing capabilities. That’s to be expected. What’s notable is LockBit’s ability to follow the trends of cloud adoption and digital acceleration, which you can see from their improved targeting ability. They were keenly aware of the growing business tolerance to data breaches, so they added DDoS as an additional threat of business disruption. They were cheeky with the tattoo PR stunt, and they showed their business savvy with their recruitment practices and repeated statements that they had no political affiliation. Their claim to be only interested in money was sometimes at odds with what was known about the group’s various affiliations. However, LockBit had many affiliates, and criminal groups like this cannot vet each member for ideology, nor can they continue to grow without creating some discontent within the ranks. LockBit was already being challenged by Royal as the dominant threat, and 3.0 had already been leaked to the public. In the absence of Operation Cronos, LockBit may have splintered into several new groups on its own.
What does it all mean?
While it is good news to hear that LockBit has been disrupted, we can’t pretend that the threat of LockBit has gone away. Spokesperson @LockBitSupp tells us everything is fine:
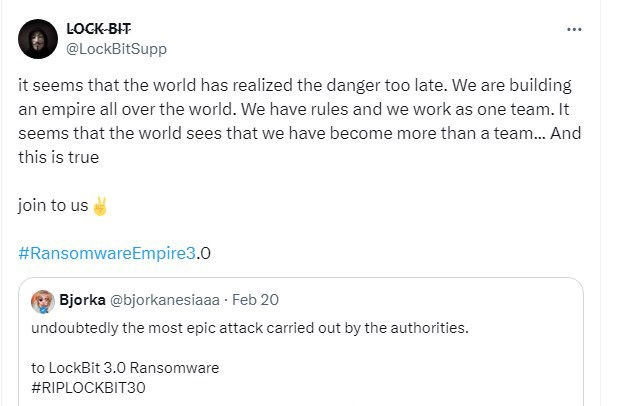
Although that is probably not true, LockBit 3.0 was leaked to the public and is in use by non-LockBit actors. Some of the LockBit infrastructure probably remains in place, but who knows how much and how effective that infrastructure is? It’s hard to predict what will happen next.
We also cannot overstate LockBit’s influence on the ransomware ecosystem in general. If you are inclined to establish a global ransomware enterprise, the LockBit operation provides many examples of what you should and should not do. LockBit-affiliated developers and distributors who remain free will continue their criminal work in other ransomware groups. In the unlikely event that everything LockBit disappears, those tattoos will still be out there, keeping the ransomware empire dream alive.
But the flip side of that coin is that threat actors everywhere just watched the mighty LockBit fall to an unprecedented international effort. There are separate multi-million-dollar rewards offered for information on LockBit, Hive, and BlackCat RaaS threat actors. Criminal charges have been filed, arrests have been made, and sanctions have been imposed. If there was such a thing as a red alert for ransomware operators, this would be it.
From the FBI press conference:
We’ll continue gathering evidence, building out our map of LockBit developers, administrators, and affiliates, and using that knowledge to drive arrests, seizures, and other operations, whether by the FBI or our partners here and abroad.
While this is, yes, a fight to protect our country, our citizens, and our national security, make no mistake—the fight for cybersecurity spans the globe. But the FBI’s presence and partnerships do, too.
So, a reminder to cybercriminals: No matter where you are, and no matter how much you try to twist and turn to cover your tracks—your infrastructure, your criminal associates, your money, and your liberty are all at risk. And there will be consequences.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.








