The SOC case files: XDR neutraliza unidad externa cargada de amenazas dirigida a MSP
Resumen del incidente
- Un proveedor de servicios gestionados (MSP) con sede en EE. UU. fue objetivo de un actor de amenaza bien equipado poco antes del festivo de Acción de Gracias.
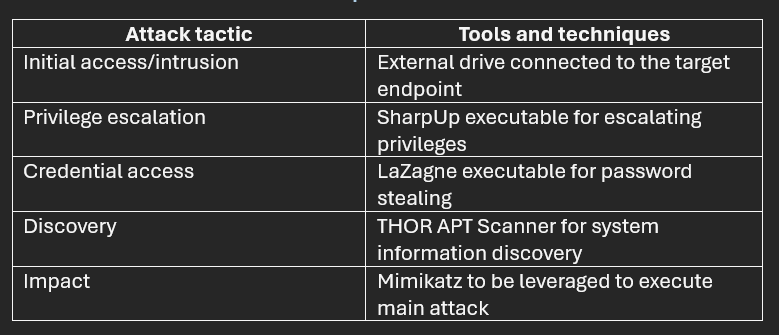
- Los atacantes conectaron una unidad externa maliciosa cargada con herramientas de hacking avanzadas a una sola estación de trabajo.
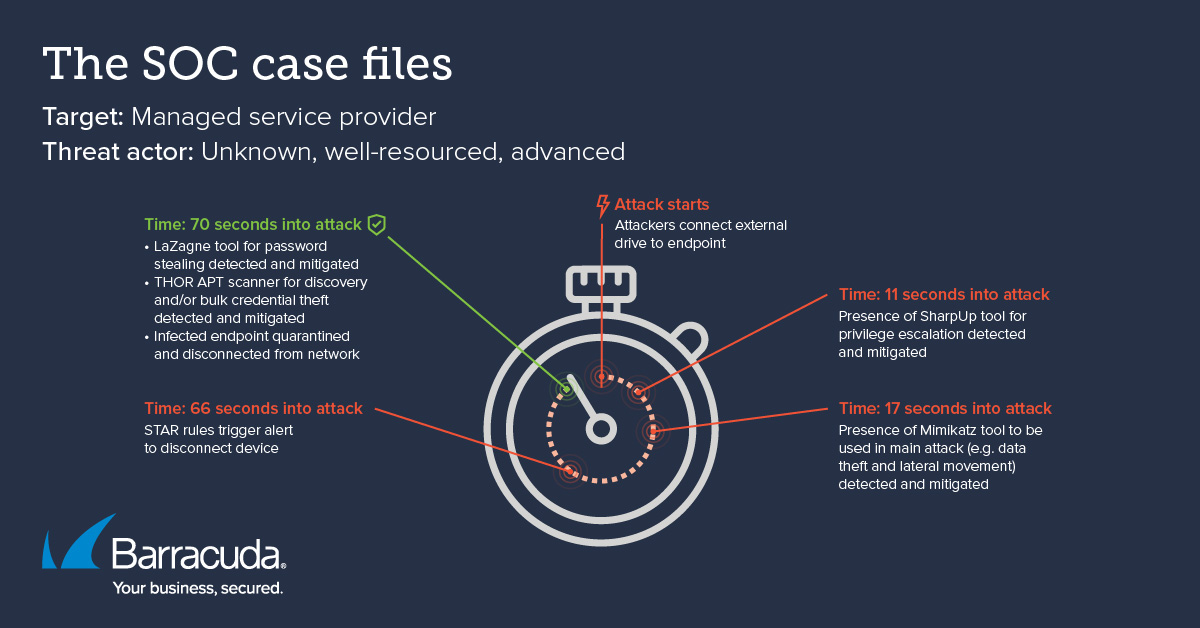
- En poco más de un minuto se mitigó la amenaza: El SOC identificó las herramientas no autorizadas, las puso en cuarentena y aisló el punto final.
El incidente fue detectado, contenido y mitigado por el Centro de Operaciones de Seguridad (SOC) 24/7 de Barracuda. El SOC es parte de Barracuda Managed XDR, un servicio de visibilidad extendida, detección y respuesta (XDR) que proporciona a los clientes servicios de detección de amenazas, análisis, respuesta a incidentes y mitigación liderados por humanos e IA las 24 horas del día para proteger contra amenazas complejas.
Cómo se desarrolló el ataque
El ataque tuvo lugar el día antes de Acción de Gracias, una importante festividad estadounidense.
- En la mañana del 27 de noviembre, los sistemas automatizados del SOC detectaron una serie de herramientas de hacking avanzadas apareciendo una tras otra en rápida sucesión en una sola estación de trabajo en la red de un MSP monitoreado.
- Las herramientas se estaban cargando en la misma carpeta de Windows desde una unidad externa no autorizada conectada a la estación de trabajo.
El principal intento de ataque
- El núcleo del intento de ataque involucró cuatro herramientas de hacking conocidas.
- El primero de estos era un ejecutable llamado SharpUp, que un atacante puede usar para intentar escalar sus privilegios en una cuenta comprometida.
- El segundo era un archivo malicioso llamado LaZagne. Esta es una herramienta de robo de contraseñas que los atacantes probablemente incluyeron en caso de que no pudieran escalar los privilegios de una cuenta comprometida utilizando SharpUp. Luego podrían usar LaZagne para intentar obtener credenciales de cuentas existentes con mayores privilegios.
- Los informes de inteligencia sobre amenazas indican que LaZagne ha sido aprovechado en ataques recientes por actores de amenazas sofisticados, incluidos los ataques persistentes avanzados (APTs) con sede en China.
- La tercera amenaza fue Mimikatz, una herramienta muy común utilizada por actores de amenazas para numerosas tareas, incluyendo la extracción de información sensible y el movimiento lateral.
- La cuarta herramienta encontrada por los analistas del SOC fue el THOR APT Scanner. Esta herramienta es utilizada típicamente por profesionales de la seguridad para identificar actividades maliciosas por parte de actores de amenazas, pero también puede ser utilizada por los propios atacantes para diversas tareas, incluyendo el robo masivo de nombres de usuario y contraseñas.
Respuesta y mitigación de amenazas
- El agente SentinelOne de XDR Endpoint Security detectó con éxito las cuatro herramientas de hacking, las marcó como amenazas y las mitigó en consecuencia.
- Las reglas personalizadas de respuesta activa de Storyline (STAR) desarrolladas por los ingenieros del SOC de Barracuda detectaron eficazmente la presencia de Mimikatz y tomaron medidas de respuesta automatizada para aislar el endpoint comprometido.
- Al aislar el punto final y terminar la conectividad de red, la amenaza fue contenida y eliminada antes de que pudieran generarse procesos maliciosos.
- El equipo SOC analizó los eventos, emitió una alerta y contactó directamente a la MSP con un resumen detallado de las detecciones y las acciones de respuesta correspondientes.
- El SOC proporcionó recomendaciones de seguridad críticas para ayudar al MSP a fortalecer la protección de su entorno, incluyendo la restricción del acceso a unidades externas.
Lecciones clave
- Los actores de amenazas son notorios por llevar a cabo ataques durante las principales festividades, momentos en los que los equipos de seguridad tradicionales pueden estar con personal reducido y las organizaciones pueden ser menos vigilantes en general.
- Los proveedores de servicios gestionados son un objetivo cada vez mayor para los actores de amenazas que entienden que, si logran vulnerar con éxito un MSP, pueden ampliar el alcance del ataque a las organizaciones cuya infraestructura de TI es gestionada por el MSP.
- Tener un SOC que opera 24/7/365, como el equipo Barracuda Managed XDR SOC, para proporcionar capacidades continuas y constantes de detección y respuesta ante amenazas es crucial.
Las principales herramientas y técnicas utilizadas en el ataque
Indicadores de compromiso (IOCs) conocidos observados en este ataque
- SharpUp SHA1: 4791564cfaecd815ffb2f15fd8c85a473c239e31
- LaZagne SHA1: 0e62d10ff194e84ed8c6bd71620f56ef9e557072
- MimikatzSHA1: d1f7832035c3e8a73cc78afd28cfd7f4cece6d20
- THOR APT SHA1: 5c154853c6c31e3bbee2876fe4ed018cebaca86f
Las características de BARRACUDA Managed XDR, como la inteligencia de amenazas, la respuesta automatizada a amenazas y la integración de soluciones más amplias, como XDR seguridad de servidor, XDR Network security y XDR seguridad en la nube, proporcionan una protección integral y pueden reducir drásticamente el tiempo de permanencia.
Para obtener más información sobre cómo Barracuda Managed XDR y el Centro de Operaciones de Seguridad pueden ayudar, por favor contáctenos.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.