Understanding the new NSA guidance on Zero Trust - Network and Environment
The National Security Agency (NSA) has released an important report outlining best practices for network and environment security within the Zero Trust model. Zero Trust emphasizes strong internal network controls to prevent attackers from moving freely within a system, even if they manage to breach the perimeter.
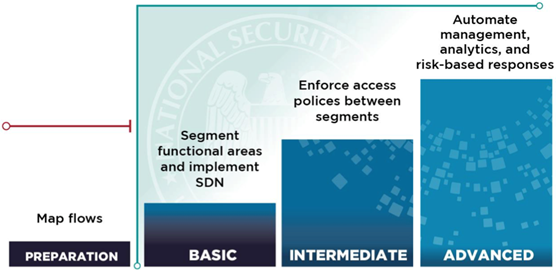
The NSA strongly recommends that organizations should proactively develop advanced security capabilities to protect their networks and data. This involves understanding data flow, implementing network segmentation, utilizing tools like software-defined networking (SDN), automating security policies, and establishing risk-based access controls.
To illustrate the importance of these recommendations, consider a real-world example highlighted in the NSA report. In 2013, a major American retail corporation suffered a significant data breach due to a lack of network segmentation. Cybercriminals gained access to the corporation's network through the credentials of a third-party HVAC vendor. Because the network lacked proper segmentation, the attackers were able to move laterally and infiltrate point-of-sale systems, stealing data from millions of credit cards. This incident demonstrates the devastating consequences of inadequate network security and highlights the critical need for Zero Trust principles.
To simplify these concepts further, we'll use a city analogy to explore the NSA's recommendations and demonstrate how they contribute to a more secure digital environment.
Building a safer city
Imagine your company's network as a dynamic city. People (users) move around, accessing buildings (data and resources) for work. Traditionally, security was like a wall around the city, keeping out the bad guys. But what if they got inside?
That's where Zero Trust comes in. It assumes bad guys are already inside and focuses on protecting each building individually. This means verifying everyone who tries to enter, even if they're already in the city.
Breaking down the city walls: Network segmentation
One key part of Zero Trust is dividing the city into smaller districts (macro-segmentation) and then further into individual blocks (micro-segmentation). This limits where people can go and minimizes damage if someone with bad intentions gets in. It's like having security guards at each building, checking IDs, and ensuring only authorized people enter.
Benefits: Implementing network segmentation offers several benefits. By limiting access to specific zones, organizations can significantly reduce their attack surface, making it much harder for attackers to move laterally and reach critical resources. Segmentation also helps contain the damage caused by a breach, preventing it from spreading to other parts of the network. Furthermore, smaller segments allow for more focused monitoring of network activity, making it easier to detect and respond to suspicious behavior.
Mapping the streets: Data flow
To effectively secure the city, we need a map of all the streets and how people move around. This is called data flow mapping. It helps us understand where data is stored, how it's used, and where it might be vulnerable.
Benefits: Understanding data flow patterns provides valuable insights into potential weaknesses in data security and access controls. With this knowledge, organizations can optimize their security controls by implementing targeted measures where they are most needed. Additionally, data flow mapping aids in incident response by helping to trace the source and impact of security incidents, allowing for faster containment and remediation.
Software-defined networking: The traffic controller
Imagine having a central traffic control system for the city. This is what software-defined networking (SDN) does. It gives us a bird's-eye view of the network and lets us control traffic flow automatically, making it easier to enforce security policies and respond to threats.
Benefits: SDN offers significant advantages for network security. By centralizing management, it simplifies the process of applying and enforcing security policies across the entire network. Additionally, automated security rules and dynamic adjustments enable faster and more effective threat response. SDN also provides enhanced visibility into network activity, making it easier to detect and investigate suspicious behavior.
SASE: A modern solution for a modern city
Managing all these security measures can be complex, but it doesn't have to be. Barracuda SecureEdge offers a modern, cloud-native Secure Access Service Edge (SASE) platform designed to simplify and strengthen your network security in a Zero Trust environment. With Barracuda SecureEdge, you can:
- Implement robust Firewall-as-a-Service (FWaaS): Safeguard your infrastructure and intellectual property with advanced firewall capabilities delivered from the cloud.
- Enable seamless access with Zero Trust Access (ZTA): Grant users secure access to applications from anywhere in the world, regardless of their location or device.
- Optimize network performance with Secure SD-WAN: Establish redundant connectivity between dispersed locations and cloud infrastructure for optimal performance and reliability.
- Enforce policies consistently: SASE applies security policies consistently across the entire network, reducing the risk of human error and misconfigurations.
- Simplify management: Instead of managing multiple security tools, SecureEdge offers a unified platform that's easier to maintain and update.
Your role as an IT admin in building an environment
As an IT admin, you play a crucial role in implementing and maintaining a Zero Trust architecture within your organization. By understanding the NSA's recommendations and leveraging solutions like Barracuda SecureEdge, you can:
- Proactively implement network segmentation to limit lateral movement and contain potential breaches.
- Conduct thorough data flow mapping to identify vulnerabilities and optimize security controls.
- Utilize SDN for centralized policy management and automated threat response.
- Stay informed about the latest cybersecurity threats and best practices to ensure your organization's defenses remain strong.
By taking a proactive approach to network security with Barracuda SecureEdge, you contribute to building a safer digital environment for your organization and its users.

Informe sobre brechas de seguridad del correo electrónico 2025
Principales hallazgos sobre la experiencia y el impacto de las brechas de seguridad del correo electrónico en organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Informe sobre perspectivas de clientes MSP 2025
Una perspectiva global sobre lo que las organizaciones necesitan y desean de sus proveedores de servicios gestionados de ciberseguridad.