
Change Healthcare and RansomHub redefine double extortion
Last month we talked about Russian threat actor ALPHV/BlackCat, a Ransomware-as-a-Service (RaaS) group that went dark after receiving a $22 million ransom payment from Change Healthcare. Today we'll catch up on what has happened since.
Let’s start with some background. The Change Healthcare attack has been in the news regularly since it was disclosed on February 21, 2024. Change Healthcare has a huge footprint throughout the healthcare sector, and it represents a single point of failure in many different places.
Change Healthcare is a technology unit within the Optum Insight business of UnitedHealth Group. Optum delivers a myriad of solutions to healthcare companies, health plans, and pharmacies. Change Healthcare was a publicly traded company offering data and analytics solutions to healthcare organizations before merging with Optum in 2022. By the time it was attacked in February 2024, Change Healthcare had over 100 applications supporting health and wellness services like pharmacy, medical record, clinical, patient engagement, payment, and more. This solution portfolio puts Change Healthcare deep into a supply chain that delivers billions of prescriptions each year. The company has access to the medical records of approximately one-third of all health patients in the United States.
The attack
Although the attack was disclosed on February 21, we don't know when the Change Healthcare systems were infiltrated. It’s common for attackers to explore the network, exfiltrate data, and establish persistent remote access before launching the ransomware encryption attack. It’s unclear how and when threat actors infiltrated the Change Healthcare systems, but we do know how ALPHV has operated in previous attacks:
Phase 1: Initial Access and Foothold (days 1 – 5). The threat actor initiated the attack by first compromising the network of a third-party vendor, utilizing a local terminal server in the client’s network as a pivot point from which to launch the attack.
Phase 2: Lateral Movement (days 6-20). The threat actor used several remote code execution techniques and the Cobalt Strike platform, to move laterally between the victim’s on-premises domains and Azure environment through RDP and tunneled connections.
Phase 3: Data Exfiltration and Additional Lateral Movement (days 27-30). Using the ‘Rclone’ tool, the threat actor exfiltrated a high volume of data from local servers to a cloud file storage service called ‘Wasabi’.
Phase 4: Extortion Attempts (days 30-45). The threat actor flooded the victim with email messages threatening to publish sensitive information if a ransom was not paid, while exaggerating the volume and sensitivity of the stolen information.
The ALPHV/BlackCat ransomware group listed Change Healthcare on their data leak site on February 28, claiming to have stolen six terabytes (6 TB) of data belonging to "thousands of healthcare providers, insurance providers, pharmacies, etc." The listing was removed later that day, leading many to speculate that Change Healthcare was negotiating with the threat actor.
These speculations appeared to be confirmed on March 1:
“There’s proof of a large amount landing in the AlphV-controlled Bitcoin wallet. And this affiliate connects this address to the attack on Change Healthcare. So it’s likely that the victim paid the ransom.”
Paying the ransom
Change Healthcare has neither confirmed nor denied paying the ransom, and that’s probably the best course of action. Paying a ransom is a sticky legal issue since the U.S. prohibits payments to threat actors sanctioned through the Office of Foreign Assets Control (OFAC). The OFAC-sanctioned ransomware criminals are listed as individuals and not threat actor groups. U.S. authorities do not care whether you do or do not know that a sanctioned individual is part of the group receiving the ransom.
It’s also a bad look for a healthcare company to give $22 million to one of the most aggressive and sophisticated threats to the health sector. You don’t want to be seen as funding future attacks against your customers and industry partners, even if the transaction is extortion.
Everyone from federal agents to IT leaders to yours truly will tell you never to pay a ransom. You can’t be sure the decryption key will work, you can’t be sure stolen data will be destroyed, and you’re likely to make yourself a target for future attacks.
“If Change did pay, it's problematic … It highlights the profitability of attacks on the health care sector. Ransomware gangs are nothing if not predictable: If they find a particular sector to be lucrative, they’ll attack it over and over again, rinse and repeat.”
Change Healthcare undoubtedly knew all of this, but still found a reason to pay. It was probably one or more of the following:
- Decryption and system restoration. The ransom paid for a decryption key that would facilitate recovery.
- Data protection. Change Healthcare paid to have the 6 TB of stolen data deleted rather than sold.
- DDoS prevention. ALPHV/BlackCat has used Distributed Denial of Service (DDoS) attacks in the past. This threat may have been added to the attack.
The ransom payment gave Change Healthcare time to focus on supporting customers and getting systems back to normal, but the ransomware drama wasn’t over yet. Remember, ALPHV was a RaaS operator. The subscribers, or affiliates, are the threat actors who deployed the ransomware and stole the victim’s data. ALPHV provided the infrastructure, which included the negotiation sites and payment system. And when the big $22 million payday hit, ALPHV ran out on their affiliates.
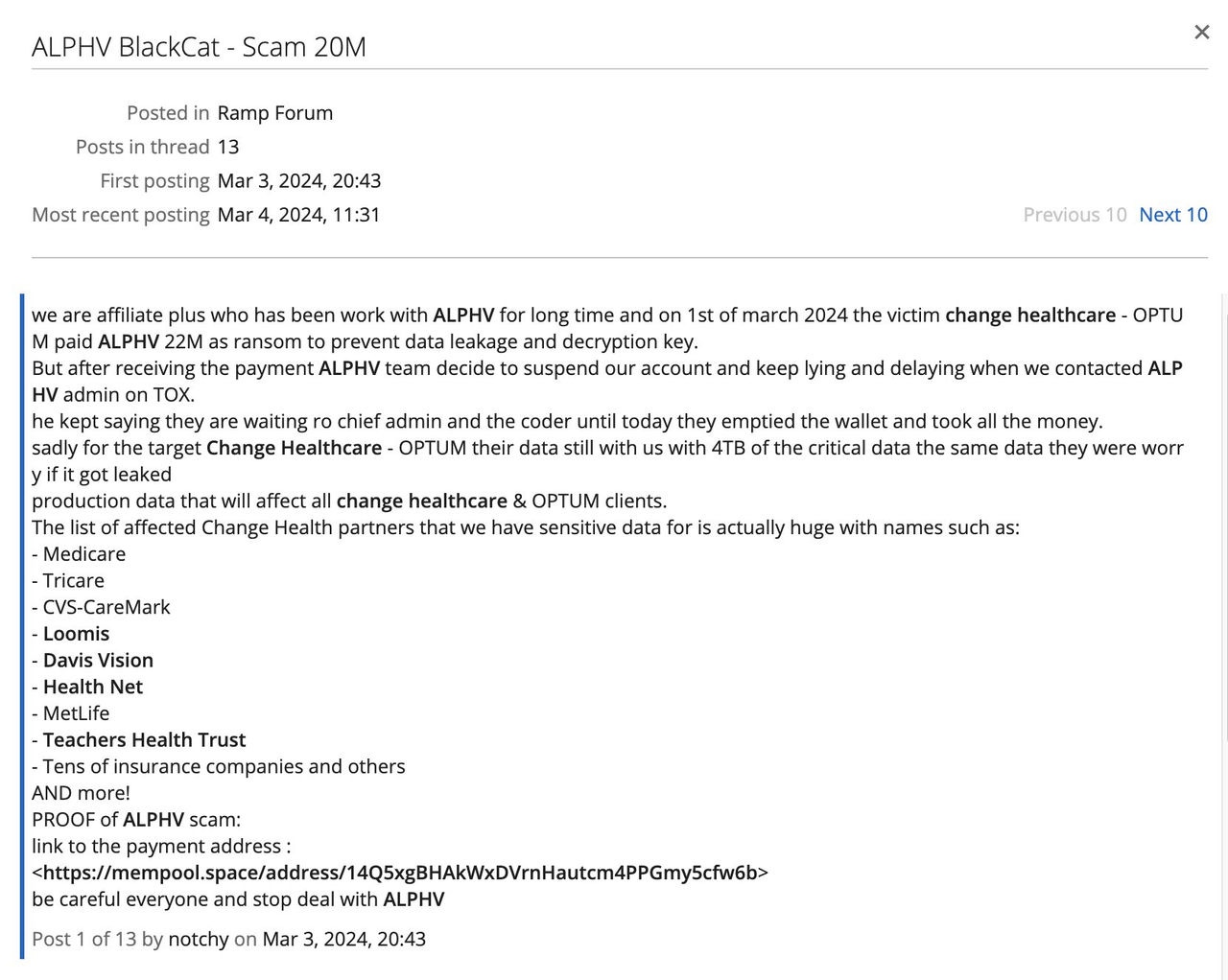
This was posted by ‘notchy,’ who claims to be the threat actor that attacked Change Healthcare. He also claims to have the data that was stolen in the attack.
While notchy was dealing with the fallout of being scammed by his fellow scammer, ALPHV quietly started the process of laundering the ransom money:
“According to blockchain intelligence firm TRM Labs, funds have recently been moved from bitcoin wallets linked to other ransoms paid to ALPHV, with these funds transferred to multiple other addresses and through a mixer, a tool used to obfuscate transactions that can be tracked on a public ledger.”
And that gets us to April 7, 2024.
RansomHub
RansomHub is a RaaS group first observed in February when it claimed responsibility for the attack on YKP Brazil. It has claimed dozens of victims since then but didn’t make a big media splash until this happened:
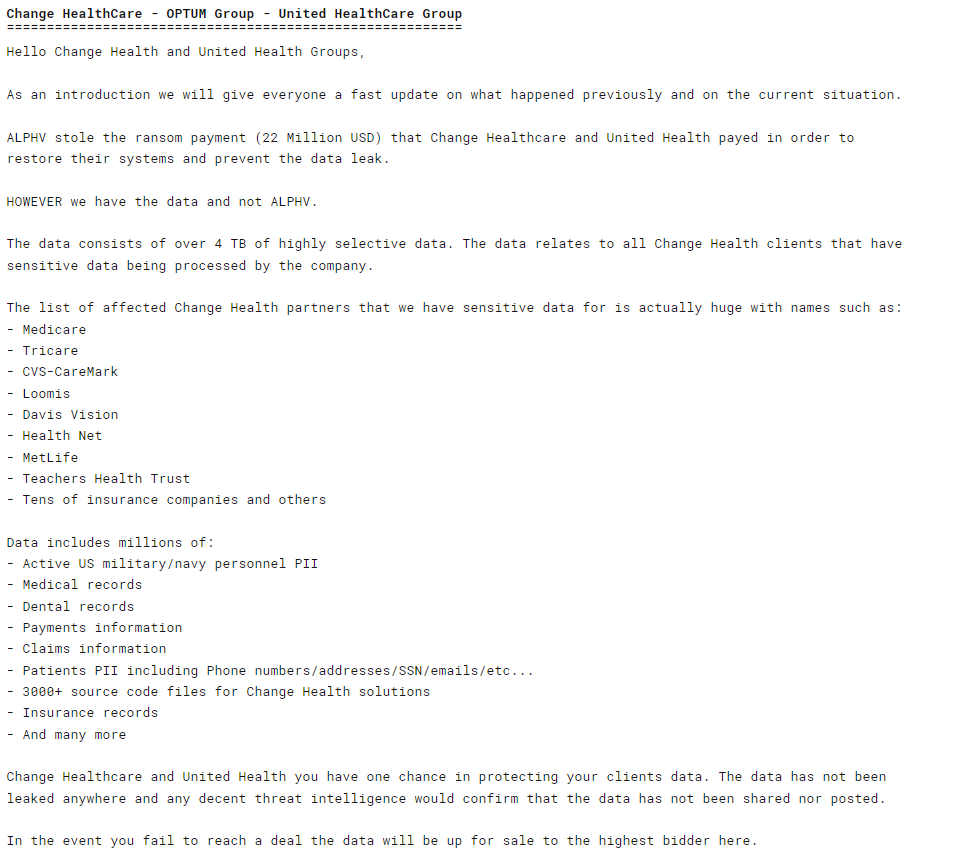
RansomHub is now demanding that Change Healthcare pay a ransom to have this data deleted rather than sold. A second extortion play around stolen data is common. Modern ransomware groups added this threat years ago. But a second extortion play around stolen data by a second threat actor? That’s unnerving. But is it real?
There are three common theories around RansomHub right now:
- RansomHub is a rebrand of ALPHV and does have the data.
- Threat actor notchy has joined RansomHub and does have the data.
- RansomHub is bluffing and does not have the data.
No one seems to know much about RansomHub. Attack data suggests that RansomHub activity spiked after ALPHV shut down, and other research shows that RansomHub follows the same rules as ALPHV:
- No attacks on non-profits.
- No attacks on anyone in a CIS or CIS-friendly state.
- No repeat attacks on a victim who has paid.
- Affiliates who violate these rules are banned.
It’s too early to determine whether RansomHub has data from the ALPHV attack. Change Healthcare confirmed that data was breached but has not confirmed or denied that data was stolen. If RansomHub’s claim is legitimate, the group will get their money, either through a ransom or an underground sale. And even if RansomHub's claim is not legitimate, millions of healthcare providers and consumers have been and will continue to be negatively affected by business decisions that Change Healthcare will neither confirm nor deny.
Barracuda Cybersecurity Platform
Barracuda offers complete ransomware protection and the industry’s most comprehensive cybersecurity platform. Visit our website to see how we defend email, network, applications, and data.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





