
City of Oakland ransomware attack results in massive data breach
The City of Oakland is still recovering from a February 8 ransomware attack that disabled or otherwise affected several systems and public services. Phone, email, and website services were disrupted, as well as payment processing and the issuing of permits and licenses. The 311 infrastructure emergency reporting system (OAK311) was unavailable for an extended period of time. Police and fire emergency services and city financial services were not significantly impacted, though there were some issues with reporting and internal communication. The city declared a state of emergency on February 14, which helped city officials tap into additional resources that aid in recovery efforts. The Oakland website has updates on service restoration.
On March 6, the city notified the public that the ransomware gang had stolen and released some of the data from the network. The FBI and third-party data specialists are working with city officials to determine the scope of the data breach. As of March 8, the leaked data is said to include the names, addresses, driver’s license numbers, and social security numbers of city employees who were on the payroll between July 2010 and January 2022. Oakland officials have asked everyone affected by this breach to monitor bank statements and credit accounts. The city will notify the affected individuals with more information.
The ransomware attack was likely caused by a phishing email deployed by the Play ransomware gang. Play, or PlayCrypt, has been active since last summer and uses a ‘big game hunting’ and double extortion attack strategy. Put simply, the Play ransomware gang targets specific victims based on desired criteria, which is usually the ability or willingness to pay a ransom. The gang steals data prior to encryption and leaves a text file with an email address to be used for negotiation. If the victim refuses to pay the ransom, the gang will leak the sensitive data. Other notable victims of Play include A10 Networks, H-Hotels (Germany), and the Belgian City of Antwerp.
The image below shows the Play ransomware extortion website announcing the City of Oakland data breach. (Source: Bleeping Computer)
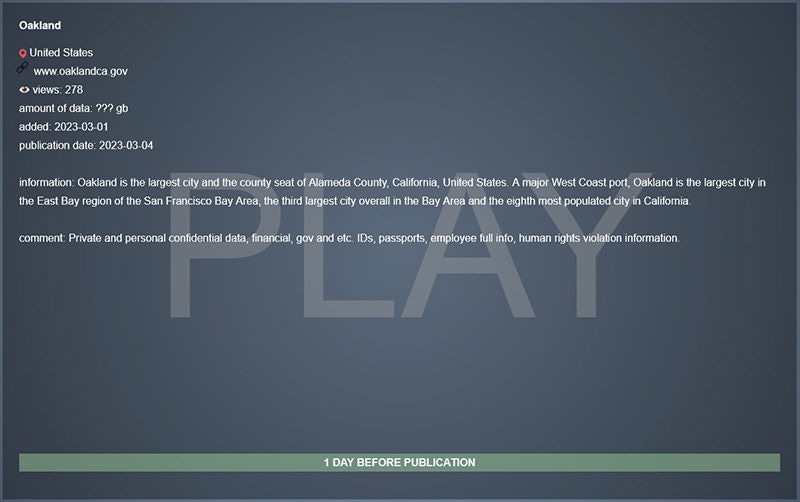
Oakland has refused to pay the ransom and has been restoring systems from backup.
Oakland now joins a growing list of local governments that have fallen victim to these ransomware gangs. Riviera Beach, Florida, and Lake City, Florida, paid the ransoms when they were attacked in 2019. Both cities had insurance to pay the bulk of the ransom demand, though paying a ransom never guarantees a positive outcome. Atlanta, Georgia, and Baltimore, Maryland, both refused to pay. Downtime and recovery costs exceeded the ransom demands, though both cities have since made significant improvements in cybersecurity.
Ransomware is a national security issue, and the United States has been getting more aggressive in fighting these gangs at the federal level and has allocated $1 billion in cybersecurity grant funds for local governments. We encourage eligible entities to prepare a cybersecurity strategy and apply for these funds when ready. Barracuda defends against ransomware attacks with comprehensive security solutions and hardened data protection. Visit our website for more information on how we can help.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





