Akira: Ransomware moderno con un toque retro
El grupo de ransomware Akira emergió en marzo de 2023 y rápidamente se estableció como un actor de amenaza formidable. Akira es una operación de ransomware como servicio (RaaS) que tiene como objetivo múltiples industrias, principalmente en los Estados Unidos y países aliados. Para el 1 de enero de 2024, Akira había "impactado a más de 250 organizaciones y reclamado aproximadamente 42 millones de dólares (USD) en ganancias de ransomware."
Los actores de amenazas de Akira han robado mucho dinero, pero sus ataques no siempre tienen éxito. Nuestro centro de operaciones de seguridad detalló recientemente un ataque fallido de Akira aquí. Utilizaremos su informe más adelante cuando exploremos la cadena de ataque de Akira.
Historia de origen
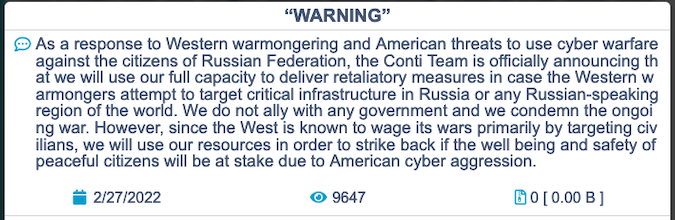
La historia de Akira comienza con el grupo de ransomware Conti, que estuvo realizando ataques desde diciembre de 2019 hasta mayo de 2022. Los analistas creen que Conti cerró sus operaciones debido a las repercusiones de el apoyo del grupo a Rusia:
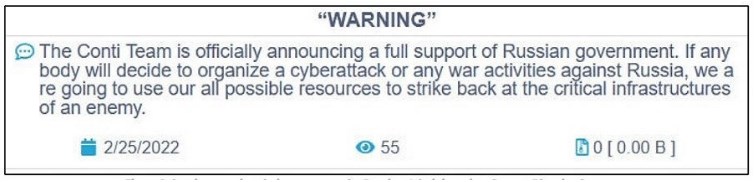
En represalia por esta muestra de apoyo, un actor no identificado filtró cientos de archivos privados de Conti, revelando direcciones de Bitcoin, mensajes privados y el manual de ransomware del grupo. Conti nunca pareció recuperarse del caos. El grupo detuvo sus ataques en mayo de 2022 y desconectó su último sitio web el mes siguiente. Utilizando los datos filtrados y el análisis de ataques, los investigadores han encontrado una larga lista de evidencias que vinculan a Akira con Conti. Esta relación no ha sido confirmada, pero muchos expertos atribuyen el éxito temprano de Akira a su acceso a los recursos y la experiencia criminal de Conti.
A diferencia de Conti, Akira no ha jurado lealtad a Rusia ni a países aliados. Akira se comunica en ruso cuando utiliza foros de la darkweb, y su ransomware incluye medidas de seguridad para evitar la ejecución en sistemas con un diseño de teclado en idioma ruso. Agregar esta evidencia a los vínculos con Conti sugiere que Akira tiene una conexión con Rusia, pero no prueba la ubicación del grupo. Tampoco es suficiente evidencia para confirmar que el grupo es de origen ruso.
Marca
Los investigadores creen que el nombre 'Akira' está inspirado en la película de anime cyberpunk de 1988 del mismo nombre, en la que el personaje titular es una fuerza incontrolable y disruptiva. La teoría predominante es que el grupo utiliza el nombre para retratarse de la misma manera.
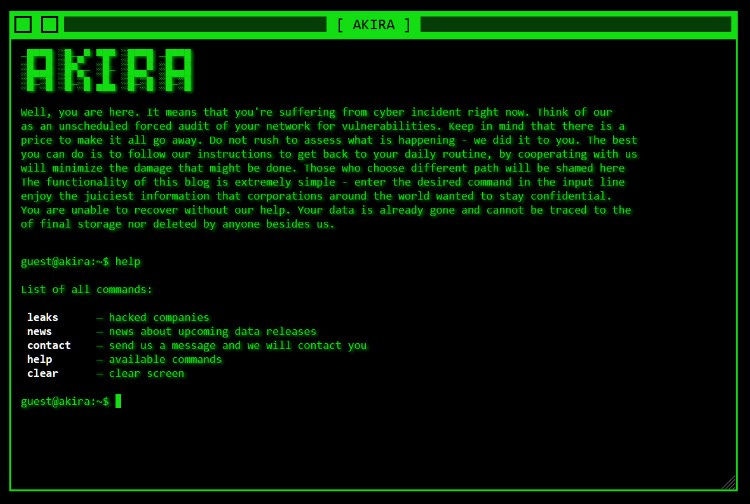
El grupo también ha adoptado una estética retro de terminal de pantalla verde para su sitio de filtración, que utiliza una interfaz de línea de comandos (CLI) para la navegación y las comunicaciones, y solo acepta cinco comandos.
Esta simplicidad y aspecto vintage ocultan el hecho de que Akira es un grupo muy sofisticado y agresivo.
Motivación
El único enfoque de Akira es el dinero. El grupo apunta a empresas pequeñas y medianas (PYME), aunque ha habido algunas víctimas más grandes y conocidas como Nissan y Universidad de Stanford.
El grupo permite ataques a todos los sectores, aunque la fabricación y la infraestructura crítica parecen ser sus favoritos.
Cadena de ataque
La cadena de ataque de Akira detalla la secuencia de eventos y herramientas que se utilizan en un ataque, desde el acceso inicial hasta la exfiltración y el cifrado de datos. Vamos a usar nuestra reciente batalla con Akira para ver cómo Akira utiliza su cadena de ataque en un ataque real contra una víctima con solo defensas parciales.
Acceso inicial:
Los expertos del SOC de Barracuda encontraron varias áreas de riesgo preexistentes en la red de la víctima, incluyendo un canal VPN abierto, dispositivos desprotegidos y un uso inconsistente de la autenticación multifactor (MFA). Estas condiciones fueron directamente relevantes para el ataque, comenzando con el acceso inicial a través de la VPN.
Escalada de privilegios y movimiento lateral
Este es un paso temprano 'posterior a la infección' en la mayoría de las cadenas de ataque, ya que los actores de amenazas intentan maximizar su alcance dentro de la red de la víctima. En nuestro caso, Akira utilizó la técnica de ‘pass-the-hash’ para obtener acceso a los sistemas de red protegidos por contraseña. Si no estás familiarizado con los hashes de contraseñas, aquí tienes un buen video introductorio.
El siguiente paso documentado por el SOC de Barracuda fue la ejecución de Advanced IP Scanner, que es una herramienta de software legítima y gratuita que enumerará los dispositivos en una red. Esto se utiliza para encontrar activos de la red y establecer movimiento lateral.
Evasión de defensa
Las técnicas de evasión de defensa de Akira se basan en una combinación de recursos para desactivar la seguridad del endpoint y las soluciones antivirus.
- PowerTool, KillAV y Terminator son programas utilizados para terminar procesos relacionados con antivirus.
- Los comandos de PowerShell se utilizan para desactivar la Protección en Tiempo Real de Microsoft Defender. PowerShell también se utiliza para eliminar archivos de Servicios de Copia de Seguridad de Volumen (VSS) antes de la encriptación.
- Las modificaciones del registro deshabilitan o reconfiguran Microsoft Defender. Otras ediciones incluyen una modificación del registro de Userlist para ocultar cuentas en la pantalla de inicio de sesión, y una modificación del registro DisableRestrictedAdmin para permitir el inicio de sesión sin credenciales.
Seguridad de Endpoint Barracuda XDR tiene capacidades anti-manipulación que impidieron que el ataque desactivara o reconfigurara su protección.
Exfiltración de datos y cifrado
Junto a los esfuerzos de evasión, Akira comenzó a ejecutar WinRar para comprimir los datos que pretende robar de la víctima. Los datos generalmente se exfiltran utilizando métodos que imitan el tráfico legítimo. Durante este evento, Akira logró obtener acceso a nivel de administrador en un servidor desprotegido. Esto les permitió lanzar su ataque de cifrado.
El ransomware intentó cifrar de forma remota los dispositivos de la red que se podían alcanzar desde el servidor no protegido. Barracuda XDR detectó esto de inmediato y desconectó todos los puntos finales protegidos de la red.
Barracuda XDR no se desplegó en toda la red de la víctima y las políticas de seguridad internas no se aplicaron de manera consistente. Puede leer sobre las consecuencias y lecciones aprendidas aquí.
Negociaciones
En un ataque exitoso, Akira dejará una nota de rescate con instrucciones para contactar al grupo. Esto permite a Akira probar sus afirmaciones y exigir un rescate. Aquí hay un ejemplo de una demanda de rescate:
Estamos dispuestos a establecer un precio de $250,000 por TODOS los servicios que ofrecemos: 1) asistencia completa para el descifrado; 2) evidencia de la eliminación de datos; 3) informe de seguridad sobre las vulnerabilidades que encontramos; 4) garantías de no publicar ni vender sus datos; 5) garantías de no atacarlo en el futuro. Hágame saber si está interesado en un trato completo o en partes. Esto afectará el precio final.
Todos sabemos que nadie debería pagar un rescate, pero también sabemos que a veces se pagan. Sin embargo, a menos que Akira cambie sus prácticas, nunca habrá una razón para pagar por el 'servicio' de informe de seguridad de Akira.
El acceso inicial a su red fue comprado en la dark web. Luego se realizó un kerberoasting y obtuvimos hashes de contraseñas. Después simplemente realizamos un ataque de fuerza bruta a estos y conseguimos la contraseña de administrador del dominio.
Esta es una declaración de copia/pega utilizada en todos los chats de negociación disponibles aquí, y va seguida de una lista de mejores prácticas. Akira no proporcionará ninguna información sobre vulnerabilidades, credenciales comprometidas o dónde se compraron las credenciales. No hay nada único para la víctima en este informe. Si estás negociando con Akira, ten esto en cuenta y revisa los últimos chats de negociación disponibles antes de pagar por este informe.
Si la víctima no paga el rescate, Akira envía un mensaje como este:
Puedes encontrarte en nuestra columna de noticias: https://akiral2iz6a7qgd3ayp3l6yub7xx2uep .... [redacted] Si deseas que esta publicación sea eliminada, tenemos que llegar a un acuerdo.
Conclusión
Realmente no hay razón para convertirse en víctima de un ataque de Akira. Este es un grupo peligroso, pero depende de brechas de seguridad que a menudo se cierran con las mejores prácticas. Si te conviertes en víctima de Akira, revisa esta información para ayudarte a prepararte para las negociaciones.
Barracuda Managed XDR y SOC proporcionan defensas integrales y en capas con visibilidad integrada y extendida. Ofrece una defensa feroz contra amenazas avanzadas como Akira, y es fácil de comprar, implementar y gestionar.
Para más información:
- Los archivos de casos SOC: XDR detecta el ransomware Akira explotando la cuenta 'fantasma' y el servidor sin protección
- Barracuda Managed XDR y SOC.

Informe sobre brechas de seguridad del correo electrónico 2025
Principales hallazgos sobre la experiencia y el impacto de las brechas de seguridad del correo electrónico en organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Informe sobre perspectivas de clientes MSP 2025
Una perspectiva global sobre lo que las organizaciones necesitan y desean de sus proveedores de servicios gestionados de ciberseguridad.