
Los archivos de casos SOC: La respuesta automatizada a amenazas de XDR ofrece protección a alta velocidad a un empleado en la nube
Resumen del incidente
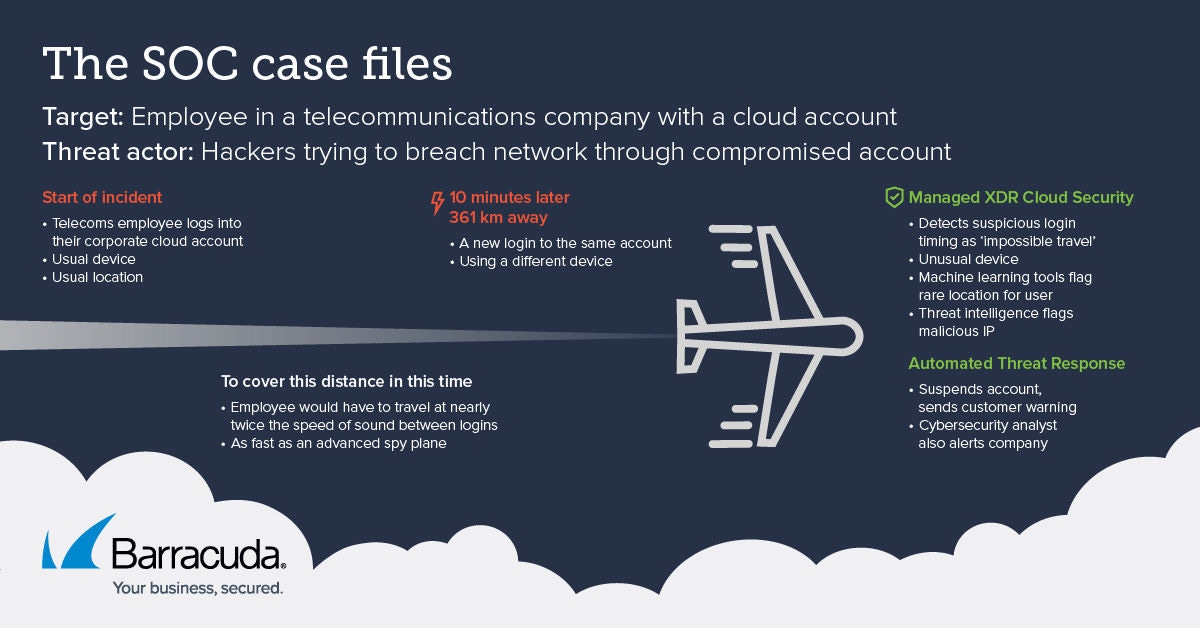
- Un empleado de una empresa de telecomunicaciones se conectó como de costumbre a su cuenta en la nube.
- Luego parecieron recorrer una distancia de 361 km, aproximadamente 225 millas, a casi el doble de la velocidad del sonido antes de volver a iniciar sesión, según los datos que llegaron a los sistemas de detección automatizados de Barracuda Managed XDR.
- Estos sistemas de detección registraron simultáneamente que:
- El segundo inicio de sesión de usuario utilizó un dispositivo diferente.
- El segundo inicio de sesión provino de una IP y ubicación que era inusual para este usuario.
- Esta IP fue marcada como maliciosa.
- En conjunto, había un 99 % de probabilidad de que la cuenta fuera comprometida por un actor de amenaza.
- Debido a que el empleador del usuario tenía Respuesta Automática a Amenazas como parte de XDR Cloud Security, la cuenta afectada se suspendió automáticamente, se alertó al cliente y se cerró el incidente.
El incidente fue detectado, contenido y mitigado por la funcionalidad de Respuesta Automática a Amenazas de Barracuda Managed XDR Cloud Security. Barracuda Managed XDR es un servicio de visibilidad, detección y respuesta extendida (XDR) que ofrece a los clientes servicios de detección de amenazas, análisis, respuesta a incidentes y mitigación, liderados por humanos y por IA, las 24 horas del día, para protegerse contra amenazas complejas.
Cómo se desarrolló el ataque
Una tarde, alrededor de las 15:25, un empleado de una empresa de telecomunicaciones se conectó a su cuenta en la nube con su dispositivo habitual y desde su ubicación habitual.
- A continuación, parecían viajar a más de 2.160 km por hora, la velocidad de un avión de reconocimiento avanzado Lockheed SR-71 Blackbird, a un lugar que rara vez habían visitado, si es que alguna vez lo hicieron, y volvieron a iniciar sesión en su cuenta usando otro dispositivo.
- Esta actividad anómala activó una serie completa de alertas en los sistemas de detección Barracuda XDR.
- El segundo inicio de sesión fue identificado como sospechoso y no autorizado.
- Exhibió cuatro características que sugieren la vulneración de la cuenta con un 99% de confianza:
- El escenario de "viaje imposible", cubriendo una distancia de 361 km (aproximadamente 225 millas) a casi el doble de la velocidad del sonido entre inicios de sesión.
- Se utilizó un dispositivo diferente en el segundo inicio de sesión sospechoso.
- Los indicadores de aprendizaje automático de Barracuda Managed XDR marcaron la dirección IP y la ubicación asociadas con el inicio de sesión sospechoso como "raras" para la cuenta de usuario afectada.
- La inteligencia de amenazas marcó la dirección IP utilizada en el evento de inicio de sesión sospechoso como posiblemente maliciosa.
Respuesta y mitigación de amenazas
- No mucho después del segundo intento de inicio de sesión, el modelo de aprendizaje automático de XDR validó las características anómalas del evento de inicio de sesión sospechoso y activó una alerta de detección maliciosa.
- Seis minutos más tarde, XDR suspendió automáticamente la cuenta afectada y emitió una advertencia de seguridad a la organización.
- Un analista de ciberseguridad del SOC hizo un seguimiento con una llamada a la organización para informarlos en persona. La organización confirmó el incidente como un positivo verdadero.
Lecciones clave
- Además de implementar soluciones de seguridad como Barracuda Managed XDR con Respuesta Automática a Amenazas y protección avanzada de correo electrónico en múltiples capas, las organizaciones pueden reforzar su protección contra tales incidentes mediante políticas sólidas y formación para empleados.
- Esto debería incluir políticas de acceso condicional, como permitir la autenticación solo desde ubicaciones autorizadas, medidas de autenticación multifactor (MFA), y cambiar las credenciales regularmente para evitar tener contraseñas obsoletas o filtradas en uso activo.
- La formación en concienciación sobre seguridad ayudará a evitar que los usuarios sean víctimas del agotamiento MFA y de ataques de phishing cada vez más complejos y evasivos.
Las características de Barracuda Managed XDR, como la inteligencia de amenazas, la respuesta automatizada a amenazas y la integración de soluciones más amplias como XDR Server Security, XDR Network Security y XDR Cloud Security, ofrecen una protección integral y pueden reducir drásticamente el tiempo de permanencia.
Para obtener más información sobre cómo Barracuda Managed XDR y el Centro de Operaciones de Seguridad pueden ayudar, por favor contáctenos.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





