
Data breaches get dangerously personal
Large data breaches are so common we refer to the last several years as the ‘post-breach era.’ We don’t need to dig into the origin or definition of that phrase to understand the meaning. Millions of sensitive records are stolen by attackers each year, and the individual owners of the stolen data are left to deal with the consequences. The company might pay a fine and give you a year of credit monitoring, but there's no guarantee the individual victims will get any further assistance.
One of the scariest things about data breaches is that the type of data being stolen goes beyond credit card information and social security numbers. Some of these breaches include deeply personal data that can be used to humiliate someone, possibly to the point of self-harm. Stolen data can be used to interfere in law enforcement, locate someone in hiding, or irreparably damage someone’s career and livelihood.
City of Oakland, 2023
We’ve discussed the Oakland ransomware attack a couple of times. The short story of Oakland is that they were attacked by Play ransomware gang on February 8. There was widespread damage to city systems and a huge loss of data that included over a decade of payroll information and other sensitive files. Play published 10GB of data on March 4 to pressure Oakland into paying a ransom. This has been followed by a 600GB batch of data, published on April 4.
The data includes details of alleged police misconduct and human rights violations, which can be troublesome for the city, the department, and individual police officers. The Oakland Police Department is operating under federal oversight due to the “Riders Scandal” of 2000, and Police Chief LeRonne Armstrong was fired on February 15 over an alleged cover-up of police misconduct. A data breach like this could lead to anything from an extension of federal oversight to the humiliation or endangerment of an officer or member of the public.
Lehigh Valley Health Network (LVHN), 2023
LVHN is a network of 13 hospitals and many other healthcare facilities in Pennsylvania. The network was attacked by the BlackCat ransomware gang, which is suspected to recruited experienced ransomware criminals from REvil and other groups. BlackCat is a Russian gang that poses a triple threat of ransomware, data theft, and distributed denial of service attacks. The gang demands a ransom using these three attacks as leverage.
LVHN confirmed the attack on February 22 and announced that it would not pay a ransom. BlackCat has since released some of the data it took from the network, including images of cancer patients receiving oncology treatments.
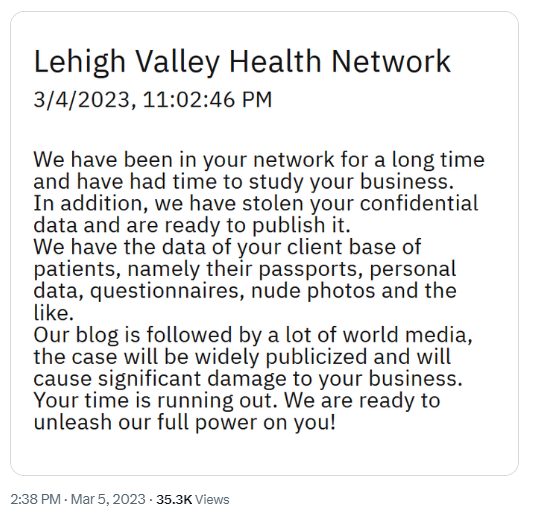
BlackCat also leaked “medical questionnaires, passports, and other sensitive patient data such as driver’s license numbers, Social Security numbers, medical diagnosis/treatment information, and lab results.” LVHN now faces a lawsuit by multiple plaintiffs who have multiple grievances, including embarrassment and humiliation. The HIPAA Journal has details of this lawsuit here.
Minneapolis Public Schools (MPS), 2023
MPS announced a ‘technology incident’ on February 21. The next update on February 24 referred to an ‘encryption event’ and noted that their investigation found no evidence that personal information had been compromised. On March 1, local news outlet KARE 11 published a statement it received from MPS:
Please note, MPS has not paid a ransom and the investigation has not found any evidence that any data accessed has been used to commit fraud. However, if the ongoing investigation indicates that personal information has been impacted, the impacted individuals will be notified immediately.
Employees and retirees were having a different experience at the time:

The Medusa ransomware gang claimed responsibility for the encryption event and released evidence of the data that was stolen. This included student names and addresses, disciplinary information, pictures of students and staff, sensitive employee information, union grievances, misconduct complaints, civil rights investigations, and more.


Los Angeles Unified School District (LAUSD), 2022
LAUSD fell victim to a Vice Society ransomware attack in early September. The attack caused significant disruption to the district but did not result in a ransom payment. In October, Vice Society published LAUSD data which included legal documents, contracts, financial reports, bank account details, and employee and student records including conviction reports and psychological assessments.
An independent investigation by The 74 later revealed that the leak included thousands of student psychological evaluations, which “offer a startling degree of personally identifiable information about students who received special education services, including their detailed medical histories, academic performance and disciplinary records.” Vice Society published this information to the dark web. The 74 states that LAUSD acknowledged this data was breached only after their investigation was published. Had these been medical records instead of education records, HIPAA and other privacy and disclosure laws would have changed the response.
The U.S. Marshals Service (USMS), 2023
USMS discovered a ransomware and data exfiltration event on February 17. Ten days later, the public affairs office announced, "The affected system contains law enforcement sensitive information, including returns from legal process, administrative information, and personally identifiable information pertaining to subjects of USMS investigations, third parties, and certain USMS employees."
The U.S. Marshals are charged with federal law enforcement and the protection of federal facilities and other resources. One of USMS's responsibilities is the operation of the Witness Security Program, also known as WITSEC, which protects government witnesses and their families. According to one senior official, the Witness Security Program database was not included in the breach, but this has been contradicted by a March 15 Bleeping Computer article showing a screenshot of WITSEC data for sale on a Russian-speaking forum. There is no evidence that WITSEC has been compromised, which leads many to speculate that the seller is trying to ‘cash in’ on the ransomware attack.
Stealing our dignity
These data breaches are dangerous. They expose the most personal information of the most vulnerable people. These criminals aren’t just stealing data that we’ve intentionally given to shopping sites or online apps. Many of these breaches violate innocent victims who would prefer this data not to exist at all. The stolen records represent embarrassing incidents, private communications, and information that is usually not given unless required by a process imposed on the victim. Psychological evaluations, cancer patient images, and details of a minor’s disciplinary or academic record? These data breaches can be humiliating. They steal our dignity. They steal us.
What can be done?
Attacks are getting more sophisticated and are increasing in volume and intensity. We are dealing with a generation of experienced cybercriminals who have built an infrastructure that allows them to grow their numbers and increase their wealth. Rival gangs are even supporting each other in pursuit of mutual goals.
How do we protect ourselves from these criminals? We’ve had a few blogs on this recently. Stefan has been discussing the important of layered defenses, and Fleming talked about the importance of security vendors sharing threat information. We’ve also published new research into attack patterns and the latest ransomware defenses.
Barracuda also advocates a three-point strategy for ransomware protection and we’ve detailed the thirteen types of email threats that lead to ransomware and other attacks. These are great resources to help you get started with a layered defense strategy or ‘gut-check’ the system you already have in place. Visit our website to see how Barracuda security and data protection solutions can help protect the data entrusted to you.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





