
Stay ahead of attackers trying to capitalize on recent bank failures
Hacking gangs are always looking for new opportunities to steal information and money. The pandemic and the war in Ukraine have proven that big headlines precede big scams. This time we’re expecting to see SMS and other phishing attacks based on the current troubles in the banking sector.
Potential banking sector ‘panic’
On March 10, the California Department of Financial Protection and Innovation (DFPI) took possession of Silicon Valley Bank on the basis of inadequate liquidity and insolvency. The DFPI then appointed the Federal Deposit Insurance Corporation (FDIC) as the receiver of Silicon Valley Bank (SVB). As the receiver, the FDIC will manage insured deposits and assume the tasks of selling assets, collecting assets, and settling debts.
The FDIC is not a bank, but it does have the authority to create a Deposit Insurance National Bank (DINB) (p.38) to act in place of the bank that failed. This type of bank is a ‘bridge bank’ that allows banking activities to continue as the failed entity moves through receivership. The Silicon Valley Bank, N.A. is the bridge bank that will conduct the remaining SVB banking activities until the FDIC can “stabilize the institution and implement an orderly resolution.” The FDIC website has the latest information on the Silicon Valley Bank failure.
A similar process took place when the New York Department of Financial Services (DFS) took possession of Signature Bank on March 12. The FDIC was appointed as receiver and established the Signature Bridge Bank, N.A., to continue bank operations.
The failure of these two banks provides an opportunity for hacking gangs to target the public with phishing and impersonation scams. We expect them to target any SVB or Signature customers who may be transferring their banking to another institution. You may also see attacks that impersonate high-profile clients of SVB, like Roku, Shopify, and Pinterest.
Bank-related SMS scams
Cybercriminals love to use SMS, or text messages, because they can make a very short message look like an urgent bank alert. Here are some examples of SMS phishing scams that impersonate other banks:
- Scam impersonating Bank of America - 'account is limited' (Source: CBS 47 Action News)
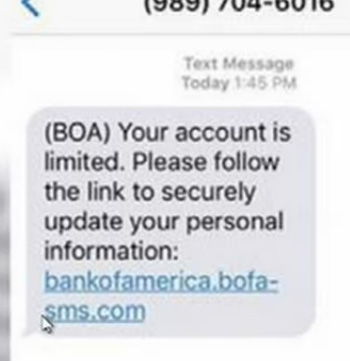
- Scam impersonating Bank of America - 'closing your account' (Source: Reader's Digest)

SMS scams may prompt you to visit a link, reply with information, or call a number. These scams are designed to steal information from you so the criminal can take control of your funds. Do not click on these links or call a number that you do not recognize. Always call the bank using the known number, visit the bank online by typing the URL manually, or use the bank’s verified mobile app.
The FDIC also warns against government imposters that may send similar messages, especially in light of the recent bank closures.
Email scams
Cybercriminals like to use email scams because email is in use everywhere. In SVB- and Signature Bank-related scams, we expect to see criminals impersonate the organizations and send emails to customers, partners, distributors, or other parties who may be waiting for new bank information. Signature Bank had dozens of offices across four states, and SVB had offices in the U.S. and several other countries. This creates a large pool of opportunity for email scammers.
Of the 13 types of email threats, we expect to see these types of attacks used in SVB-, Signature Bank-, and FDIC-related scams:
- Impersonation: Domain and brand impersonation are designed to trick the recipient into thinking the email is from a known and trusted sender.
- Phishing: This attack will attempt to steal bank login credentials, PIN and account numbers, and other sensitive information.
- Malware: Malicious software hidden in an email or email attachment and is often combined with a phishing attack. The malware can also be downloaded from an external website by a malicious script that is embedded in the email.
- Account takeover (ATO): This type of fraud occurs when a malicious actor gains access to a legitimate user’s account credentials through a phishing attack or some other data leak. If this is a business account, the attack can collect information on company operations, distribute malware, commit wire fraud, or launch a ransomware attack.
- Business email compromise (BEC): Criminals impersonate someone in an organization to defraud the company, its employees, customers, or partners. This usually involves the diversion of funds from a legitimate recipient to the criminal. This type of attack is often made possible by successful phishing attacks.
These are not the only attacks that we will see, but they are probably going to be the most common.
Current bank-related threats
Barracuda Security Operations Center monitors threats all over the world. Here are some examples of bank attacks that we can share:
- The threat actor is impersonating a partner attempting to make a payment. The attachment bank-info.doc is designed to steal sensitive account information:

- The threat actor is impersonating an employee who needs to update his bank account right away. If Janet replies, the attacker can use the information to divert payroll funds:

- This is a common and simple scam in which the attacker wants the victim to click on a link to make an overdue payment. The link will take the victim to a phishing site that will steal information along with the money that is paid:

Protecting yourself and your company from these scams
We recommend you adopt the following practices and take immediate action on email security:
- Do not click on links in an email or text message.
- Do not share personal information via incoming phone call or email. Legitimate organizations do not solicit this information in an unsecured manner.
- Be on guard against unusual requests for information or money. If you would like to contact the sender, find the contact information yourself rather than using the contact information in the message.
- Use secure communication to reach out for all changes related to a bank or other financial institution. This may require an in-person visit or video conference that facilitates proper identification of both parties.
- Prevent your domain from being impersonated through email by using tools like SPF, DKIM, and DMARC enforcement policy.
- Deploy an AI-enabled anti-phishing and impersonation protection solution. This type of security detects the malicious intent of a message by analyzing multiple data points.
- Use an email encryption service that tracks sender and receiver with full authorization and recipient validation.
Given today’s macroeconomy and evolving fiscal policies, it's imperative to train our users to be extra cautious when dealing with financial transactions, including email conversations. During these serious financial crises, regardless of impact, it’s also important to communicate with your customers, business partners, and vendors to establish a trusted communication channel so information can be shared. Improving your email security posture — especially utilizing better tools for detection, prevention, and response — will help you stay ahead of the attackers.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





