
The Zero Trust Maturity Model
Note: This is part five of a five-part series on the origins and tenets of Zero Trust.
Over the past few weeks, we’ve covered the origins and core tenets of Zero Trust. As you plan your implementation, you should also be familiar with the Zero Trust Maturity Model outlined by the Cybersecurity & Infrastructure Agency (CISA). This model is a roadmap that helps companies transition through full deployment of Zero Trust in alignment with the NIST tenets.
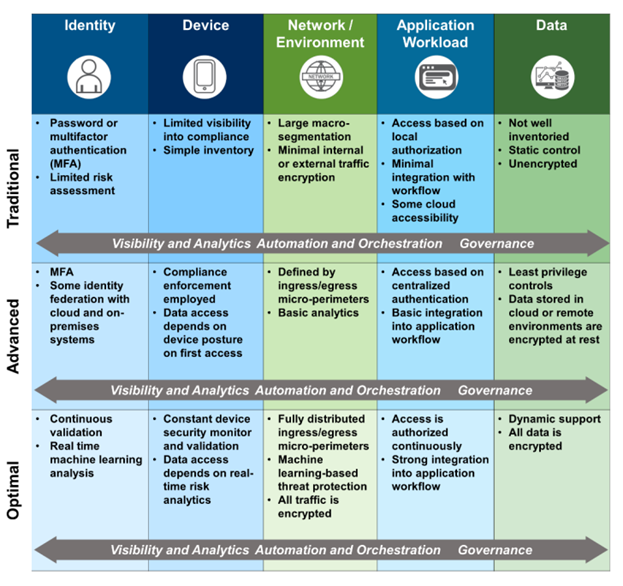
CISA identifies five distinct pillars for Zero Trust implementation:
- Identity: An attribute or set of attributes that uniquely describe an agency user or entity
- Device: Any hardware asset that can connect to a network, including internet of things (IoT) devices, mobile phones, laptops, servers, and others
- Network: An open communications medium, including agency internal networks, wireless networks, and the internet, used to transport messages
- Application workload: Systems, computer programs, and services that execute on-premises, as well as in a cloud environment
- Data: Data should be protected on devices, in applications, and in networks
The maturity model represents a gradient of implementation across these pillars, which means that deployment can begin on each pillar independently and at different times. The company-wide Zero Trust deployment can proceed this way until it has reached the point where automation, visibility, and dynamic policy creation require the integration of all five pillars.
Three stages of maturity
To support the gradient nature of the model, CISA has outlined three maturity stages for each pillar:
- Traditional: Manual configurations and static security policies
- Advanced: Centralized visibility, identity control, and policy enforcement based on some cross-pillar coordination
- Optimal: Fully automated assigning of attributes to assets and resources, dynamic policies based on automatic triggers, and alignment with open standards for cross-pillar interoperability
The CISA document provides this summary of each pillar at each maturity stage:
A proper Zero Trust deployment will save your company time and money, and help you maintain a secure environment that’s in compliance with regulatory requirements.
Resources
For more information on Zero Trust and Barracuda Zero Trust solutions, visit these resources:
- Time to build your Zero Trust Architecture
- Barracuda CloudGen Access: Enable Zero Trust Access from any device, anywhere
- Secure Access Service Edge (SASE): Accelerate and secure cloud migrations.
- On-demand webinar: Barracuda | Vandis | AWS Dev Day: Advanced Zero Trust Access Control
- CISA Zero Trust Maturity Model
- NIST Special Publication 800-207
- The Open Group Zero Trust Core Principles
For assistance with your Zero Trust deployment, contact us at www.barracuda.com
This is the final post in this five-part series. The entire series is available here.

Informe sobre brechas de seguridad del correo electrónico 2025
Principales hallazgos sobre la experiencia y el impacto de las brechas de seguridad del correo electrónico en organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Informe sobre perspectivas de clientes MSP 2025
Una perspectiva global sobre lo que las organizaciones necesitan y desean de sus proveedores de servicios gestionados de ciberseguridad.





