
Data dumps: A lucrative niche
Earlier this year Internet security researcher Rajshekhar Rajaharia revealed several large data breaches by the same criminal who dumped the data from the Juspay breach. Rajaharia is the researcher who discovered and reported that Juspay, a payment processing company for retailers like Amazon, Uber, Swiggy, and MakeMyTrip, was compromised in August 2020. The data breach involved the records of 35 million consumers, including username, card type, the bank that has issued the card, card expiry date, and partially unmasked card number, among other details. Juspay reports that the data cannot be used to make transactions, and the company has taken steps to increase security.
10 Crore Indian Cardholder's Cards Data Including Name, Mobile, BankName Leaked from @juspay Server. Available for Sell on DarkWeb.
Story - https://t.co/WczIrFeLel #Infosec #DataLeak #DataBreach #infosecurity #CyberSecurity #GDPR #DataSecurity #Banks #CreditCard #dataprotection pic.twitter.com/X1KYcP8WSh
— Rajshekhar Rajaharia (@rajaharia) January 3, 2021
The additional incidents Rajaharia revealed involve Chqbook, Big Basket, and more. All these databases have information up through August 2020, and the data was for sale on the dark web. Rajaharia has been able to verify that some of the leaked data is authentic.
Same hacker who was selling @JusPay DB now selling DBs of more Indian companies on Dark Web. @clickindia - 8Mn @chqbook - 1Mn @wedmegood - 1.3Mn. Same Hacker also selling @bigbasket_com too. May be a strong connection between all these recent data leaks. #InfoSec #DataLeak #GDPR pic.twitter.com/zs0mA7NjLR
— Rajshekhar Rajaharia (@rajaharia) January 6, 2021
A lucrative criminal niche
Data breaches and data dumps are nothing new. The first large data breach was reported in 2004 when an America Online (AOL) employee stole 92 million customer account screen names, ZIP codes, phone numbers, and credit card types. This data wasn’t exactly dumped, though; the records were sold to a spammer, and then resold multiple times to other spammers. The data was eventually sold to an informant, and two of the spammers were ultimately prosecuted under the new federal anti-spam law. The AOL incident made a couple of things clear to criminal hackers and spammers:
- Law enforcement was serious about cybercrime
- Data could be monetized several times before losing value
The rise of a global dark web helped criminals with both of these issues. Criminals are harder to identify, their operations may be run from a different jurisdiction, and the criminal marketplace makes it easy for them to reach and negotiate with potential buyers. The Juspay data dump was listed for $8,000 and ultimately sold for $5,000.
The value of a partial record
 Data sets that are current and include an email, password, and other sensitive personal information are always going to be valuable to criminals. But the Juspay data is several months old, there are no passwords, and these records can’t be used to make purchases because most of the credit card information is masked with a hash function. Why would anyone pay $5,000 for the set?
Data sets that are current and include an email, password, and other sensitive personal information are always going to be valuable to criminals. But the Juspay data is several months old, there are no passwords, and these records can’t be used to make purchases because most of the credit card information is masked with a hash function. Why would anyone pay $5,000 for the set?Rajshekhar Rajaharia has answered that for us too: “If the hash values of the cards are cracked, even two years from now, all this data can be leaked on the dark web.” This is something that is possible through brute force hacking or a leak from a careless or disgruntled Juspay employee.
Multiple partial data dumps can be combined as well, allowing a criminal to match names and email addresses from one data dump to a complete set of login credentials in another. The sets would only need to have one field in common for the hacker to combine the records successfully. A 2019 IBM report states that the average size of a data breach is 25,575 records. Even if only half of the records from an average size data dump can be matched to each other, that’s thousands of potentially compromised user accounts, payment data, and other sensitive records. This kind of access can harm the individual for years as personal information gets used and sold to new criminals over a long period of time.
The business perspective
No company wants a data breach; it’s embarrassing to explain and harmful to relationships with consumers, suppliers, and employees. It’s also expensive when you factor in remediation, downtime, compliance costs, and lost business from future customers who no longer trust your brand. This lack of trust may grow over time, as data stolen from your business can be used in certain types of attacks to steal the data of a different company. A well-known example of this is the Target data breach, which was made possible when the attackers were able to steal credentials from Target's HVAC vendor, Fazio Mechanical Services. These credentials were used to access a web application on Target’s internal network. This provided the criminals with access to Target’s POS systems and data.
The 2020 Verizon Data Breach Investigations Report identifies eight actions that lead to data breaches:
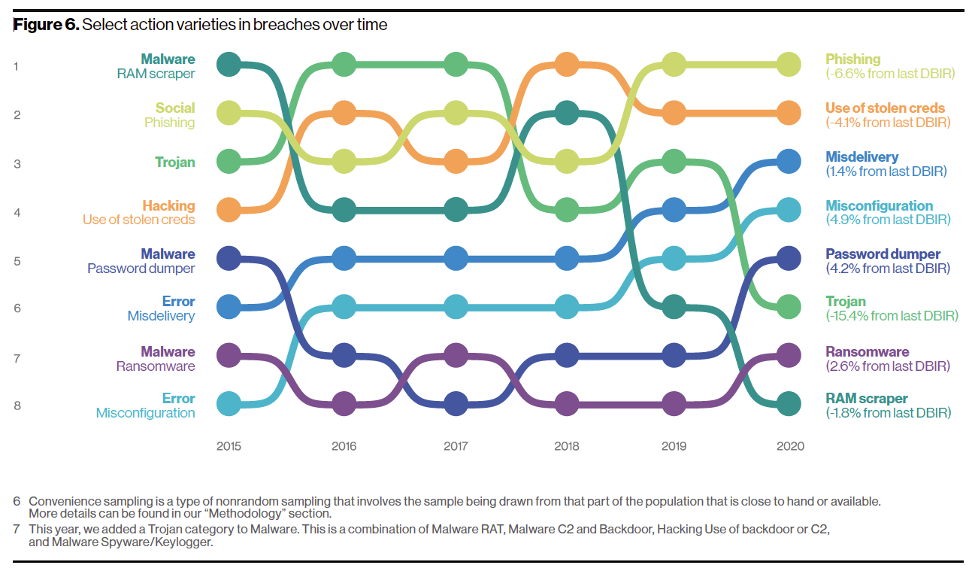
- Misdelivery: Human error resulting in data being sent to the wrong recipient
- Misconfiguration: Internet-facing assets are compromised because they were not secured properly
- Password dumper: A type of malware that extracts encrypted passwords from a host computer
- Ransomware: Malware that encrypts files and launches a demand for payment in exchange for decryption
Protect your data
The top data breach attacks take advantage of multiple threat vectors, and IT teams need to make sure that these threat vectors are continuously defended from the latest attacks. Barracuda solutions defend against network, application, and email attacks, and protect company data on-premises or in the cloud. Many of our products are available in the Azure and AWS Marketplaces, and all have 30-day free trials.

Informe de Barracuda sobre Ransomware 2025
Principales conclusiones sobre la experiencia y el impacto del ransomware en las organizaciones de todo el mundo
Suscríbase al blog de Barracuda.
Regístrese para recibir Threat Spotlight, comentarios de la industria y más.

Seguridad de vulnerabilidades gestionada: corrección más rápida, menos riesgos, cumplimiento normativo más fácil
Descubra lo fácil que es encontrar las vulnerabilidades que los ciberdelincuentes quieren explotar.





